Hard skills are technical, measurable abilities like network configuration, troubleshooting, and security protocol implementation that a network engineer should highlight.
Popular Network Engineer Resume Examples
Check out our top network engineer resume examples that showcase key skills such as network design, troubleshooting, and security management. These examples highlight how to effectively present your experience and achievements in the tech industry.
Ready to build your ideal resume? Our Resume Builder offers user-friendly templates designed specifically for networking professionals, helping you shine in your job applications.
Recommended
Entry-level network engineer resume
The entry-level resume successfully emphasizes the job seeker’s achievements in network optimization and security, demonstrating their ability to support cost-saving strategies and infrastructure improvements. Entry-level network engineers should highlight a strong grasp of network systems, certifications, and project experience that showcases proactive problem-solving skills.
Mid-career network engineer resume
This resume adeptly highlights the job seeker's technical skills and achievements, showcasing their ability to manage complex networks and drive efficiency improvements. The strategic presentation of roles demonstrates a clear career trajectory towards advanced responsibilities in network engineering.
Experienced network engineer resume
The work history section illustrates the applicant's expertise as a network engineer, showcasing significant achievements such as improving network speed by 25% and reducing downtime by 20%. The clear formatting with bullet points improves readability, making it easy for hiring managers to identify key accomplishments quickly.
Resume Template—Easy to Copy & Paste
Min Kim
Detroit, MI 48212
(555)555-5555
Min.Kim@example.com
Professional Summary
Accomplished Network Engineer skilled in network design and optimization. Proven track record in enhancing network security and efficiency. Expert in VPN and cloud integration.
Work History
Network Engineer
TechWave Systems - Detroit, MI
January 2024 - October 2025
- Implemented network upgrades for 20% performance boost
- Designed secure VPNs, reducing breaches by 30%
- Optimized routing, cutting latency by 15ms
Systems Network Coordinator
NetComm Solutions - Southgate, MI
January 2021 - December 2023
- Led firewall deployments for 500 users
- Managed cloud migrations saving 12K annually
- Automated network monitoring improving uptime
Network Analyst
CyberNet Innovations - Detroit, MI
January 2019 - December 2020
- Conducted daily network diagnostics reports
- Resolved technical issues reducing downtime by 35%
- Configured routers enhancing security protocols
Languages
- Spanish - Beginner (A1)
- Chinese - Beginner (A1)
- French - Intermediate (B1)
Skills
- Network Design
- VPN Configuration
- Firewall Management
- Cloud Integration
- Network Security
- Routing Optimization
- Troubleshooting
- Technical Documentation
Certifications
- Cisco Certified Network Professional (CCNP) - Cisco Systems
- Certified Network Security Specialist - International Network Security Organization
Education
Master of Science Computer Networking
Massachusetts Institute of Technology Cambridge, MA
May 2019
Bachelor of Science Information Technology
University of California, Berkeley Berkeley, CA
May 2017
How to Write a Network Engineer Resume Summary
Your resume summary is the first thing employers will see, making it essential to create a positive impression by aligning your skills with the job requirements. As a network engineer, you should emphasize your technical expertise and problem-solving abilities in this section.
Highlight your experience with network design, troubleshooting, and various technologies that showcase your qualifications. This is where you can demonstrate how you've contributed to previous projects and improved system performance.
To help you craft a powerful summary, consider these examples that illustrate what works effectively and what may fall short:
I am a dedicated network engineer with extensive experience in the field. I seek a position that allows me to use my skills and contribute positively to the company. A role with good benefits and room for advancement would be perfect for me. I believe I can make a significant impact if given the chance.
- Lacks specific details about technical skills or achievements, making it too vague
- Overuses personal language, which detracts from professionalism and clarity
- Emphasizes what the applicant desires rather than highlighting their potential contributions to the employer
Results-driven network engineer with 7 years of experience in designing and implementing robust networking solutions for enterprise environments. Improved network uptime by 20% through proactive monitoring and optimization strategies, leading to improved system performance and user satisfaction. Proficient in Cisco routers and switches, network security protocols, and cloud-based technologies.
- Begins with a clear statement of experience level and area of expertise
- Highlights a quantifiable achievement that illustrates the applicant's impact on network reliability
- Includes relevant technical skills that align with industry standards, showcasing competency in essential areas
Pro Tip
Showcasing Your Work Experience
The work experience section is important for your resume as a network engineer, serving as the primary focus with the bulk of your content. Good resume templates consistently feature this essential section.
This part should be organized in reverse-chronological order, highlighting your previous roles. Use bullet points to succinctly convey your achievements and contributions in each position.
We’ll now present a couple of examples that illustrate effective work history entries for network engineers. These examples will clarify what works well and what should be avoided:
Network Engineer
Tech Solutions Inc. – Austin, TX
- Managed network systems.
- Troubleshot issues and fixed problems.
- Worked with team members on projects.
- Documented processes and procedures.
- Lacks specific details about the technologies used or projects handled
- Bullet points are vague and do not highlight personal contributions or achievements
- Focuses on routine tasks rather than demonstrating impact or results in network performance
Network Engineer
Tech Solutions Inc. – San Francisco, CA
March 2020 - Current
- Design and implement robust network infrastructure supporting over 500 users, improving system uptime by 30%.
- Lead troubleshooting efforts that reduced network latency by 40%, improving end-user experience significantly.
- Develop training materials for junior engineers, fostering skill development and increasing team efficiency by 20%.
- Uses strong action verbs to convey the job seeker's contributions clearly
- Incorporates specific metrics to demonstrate tangible improvements in performance
- Highlights relevant technical skills while showcasing leadership and training capabilities
While your resume summary and work experience are important components, don't overlook the importance of other sections that contribute to a well-rounded presentation. For more detailed insights on crafting each part of your resume, be sure to explore our comprehensive guide on how to write a resume.
Top Skills to Include on Your Resume
A skills section is important for showcasing your qualifications and grabbing the attention of potential employers. It provides an opportunity to emphasize your skills, making it easier for hiring managers to understand how you align with the role.
For a network engineer, balance a blend of hard and soft skills alongside technical abilities such as expertise in networking protocols, experience with routers and switches, and familiarity with tools like Cisco IOS or Wireshark. Highlighting these specific skills showcases your capability in maintaining and optimizing network systems.
Soft skills, such as problem-solving, teamwork, and communication, are important for collaborating with diverse teams and ensuring seamless network operations.
Selecting the right resume skills is important for aligning with what employers expect in an applicant. Many organizations rely on automated systems to filter out applicants who lack essential qualifications needed for the position.
To effectively highlight your strengths, carefully review job postings to identify which skills are emphasized. This approach not only captures the attention of recruiters but also ensures you meet the criteria set by ATS systems.
Pro Tip
10 skills that appear on successful network engineer resumes
Improve your resume to attract recruiters by highlighting the most sought-after skills for network engineers. You can see these skills illustrated in our resume examples, which will help you apply for jobs with greater confidence.
Here are 10 essential skills you should think about including in your resume if they align with your experience and job requirements:
Network configuration
Troubleshooting
Firewall management
VPN setup
Routing protocols knowledge
Performance monitoring
Cloud computing expertise
Technical documentation skills
Team collaboration
Cybersecurity awareness
Based on analysis of 5,000+ engineering professional resumes from 2023-2024
Resume Format Examples
Choosing the appropriate resume format is important for network engineers, as it highlights essential technical skills, relevant experience, and career growth to attract potential employers' attention.
Functional
Focuses on skills rather than previous jobs
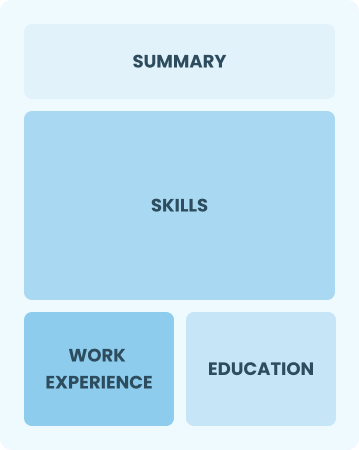
Best for:
Recent graduates and career changers with limited experience in networking
Combination
Balances skills and work history equally
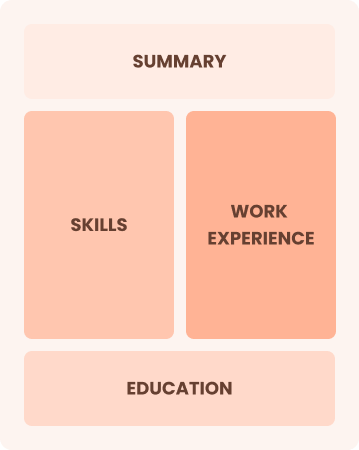
Best for:
Mid-career professionals focused on demonstrating their skills and potential for growth
Chronological
Emphasizes work history in reverse order

Best for:
Engineers excelling in network architecture and team leadership
Frequently Asked Questions
Should I include a cover letter with my network engineer resume?
Absolutely, including a cover letter can significantly improve your application. It allows you to showcase your personality and clarify how your skills align with the job. If you need assistance, explore our comprehensive guide on how to write a cover letter or use our Cover Letter Generator for a quick start.
Can I use a resume if I’m applying internationally, or do I need a CV?
When applying for jobs outside the U.S., use a CV instead of a resume. A CV is often required in many countries and provides more detailed information about your academic and professional history. To ensure your application meets international expectations, explore our CV examples and guides on how to write a CV.
What soft skills are important for network engineers?
Soft skills like communication, problem-solving, and teamwork are essential for network engineers. These interpersonal skills facilitate collaboration with colleagues and clients, ensuring effective troubleshooting and project execution while fostering a positive work environment.
I’m transitioning from another field. How should I highlight my experience?
Highlight your transferable skills such as teamwork, analytical thinking, and adaptability when applying for network engineer positions. By showcasing these abilities, you demonstrate your potential value to employers even if you have limited direct experience. Use concrete examples from previous roles to show how these strengths align with tasks like troubleshooting network issues or collaborating on projects.
How do I write a resume with no experience?
Even if you have limited experience as a network engineer, you can write an effective resume with no experience by highlighting relevant coursework, certifications, and personal projects. Emphasize your problem-solving skills and eagerness to learn about networking technologies. Your passion for technology and ability to adapt will resonate with employers looking for potential over experience.
Should I include a personal mission statement on my network engineer resume?
Yes, including a personal mission statement on your resume is advisable. It effectively conveys your core values and professional aspirations. This approach shines particularly in organizations that prioritize innovation and teamwork, making it a strong fit for companies with collaborative cultures.







