Hard skills, such as systems design, data analysis, and database management, enable a systems analyst to effectively optimize and implement IT solutions.
Popular Systems Analyst Resume Examples
Check out our top systems analyst resume examples that emphasize critical skills such as data analysis, problem-solving, and effective communication. These samples provide a solid foundation for showcasing your qualifications to potential employers.
Ready to build your impressive resume? Our Resume Builder offers user-friendly templates designed specifically for technology professionals, helping you make a lasting impression in your job hunt.
Recommended
Entry-level systems analyst resume
This entry-level resume for a systems analyst effectively showcases the job seeker's technical skills and accomplishments, including significant efficiency improvements and cost savings achieved in previous roles. New professionals must demonstrate a strong understanding of system optimization and data analysis capabilities, as well as their ability to contribute to operational enhancements, even with limited work experience.
Mid-career systems analyst resume
This resume effectively outlines key qualifications by showcasing a solid mix of technical expertise and leadership experience. The measurable impacts from previous roles indicate the job seeker's readiness for more complex challenges, reflecting growth and capability in systems analysis.
Experienced systems analyst resume
The work history section illustrates the applicant's strong background as a systems analyst, emphasizing significant achievements like improving system efficiency by 30% and reducing downtime by 20%. The use of bullet points improves readability, making it easy for recruiters to quickly identify key accomplishments.
Resume Template—Easy to Copy & Paste
Ming Chen
San Diego, CA 92111
(555)555-5555
Ming.Chen@example.com
Skills
- Systems Optimization
- Technical Analysis
- Project Management
- Problem Solving
- Data Analysis
- Budget Management
- Workflow Automation
- Stakeholder Engagement
Certifications
- Certified Systems Analyst - International System Analyst Council
- Project Management Professional (PMP) - Project Management Institute
Languages
- Spanish - Beginner (A1)
- German - Intermediate (B1)
- French - Beginner (A1)
Professional Summary
Dynamic Systems Analyst with 4 years of experience. Proven in enhancing efficiency, optimizing processes, and delivering tech solutions in high-impact settings.
Work History
Systems Analyst
TechVision Solutions - San Diego, CA
January 2024 - October 2025
- Increased system efficiency by 30%
- Reduced downtime by 15% through tech updates
- Managed budgets over 100K quarterly
IT Consultant
Innovatech Services - San Francisco, CA
January 2023 - December 2023
- Optimized workflows boosting output 25%
- Trained teams improving skills by 50%
- Developed tech solutions increasing ROI 20%
Business Systems Analyst
DigitalEdge Consulting - Riverside, CA
January 2021 - December 2022
- Streamlined processes cutting costs by 10%
- Integrated tools enhancing productivity 15%
- Led project teams achieving goals 5 months early
Education
Master of Science Information Systems
Stanford University Stanford, California
June 2021
Bachelor of Science Computer Science
University of Texas Austin, Texas
May 2019
How to Write a Systems Analyst Resume Summary
Your resume summary is the first opportunity to make a lasting impression on hiring managers. It should succinctly reflect how your skills and experiences align with the systems analyst role.
As a systems analyst, it’s essential to highlight your analytical abilities, technical knowledge, and problem-solving skills. Showcase your experience in optimizing processes and improving system efficiency.
To guide you in crafting an effective resume summary, consider these examples that illustrate what works well and what should be avoided:
I am a dedicated systems analyst with years of experience in various industries. I seek a position where I can use my analytical skills and contribute to the company’s success. A supportive environment that promotes teamwork and personal development is important to me. I believe I would be a great fit for your team.
- Lacks specific details about the applicant's actual skills or achievements, making it vague
- Uses generic expressions like 'dedicated' and 'great fit', which do not differentiate the job seeker
- Concentrates on what the job seeker desires from the job rather than highlighting their value to potential employers
Detail-oriented systems analyst with 6+ years of experience in optimizing IT infrastructure and improving system performance for healthcare organizations. Successfully led a project that improved data processing efficiency by 30%, resulting in faster decision-making processes. Proficient in SQL, data modeling, and using analytical tools to drive informed business strategies.
- Begins with specific experience duration and focus area within the IT sector
- Highlights a quantifiable achievement that showcases direct impact on organizational efficiency
- Mentions relevant technical skills that align with industry needs, demonstrating strong qualifications
Pro Tip
Showcasing Your Work Experience
The work experience section is important in your resume as a systems analyst, serving as the main focus and where you’ll present most of your content. Good resume templates always emphasize this important section.
This part should be structured in reverse-chronological order, detailing your previous roles. Use bullet points to highlight your key achievements and contributions in each job.
To help illustrate effective work history entries, we have provided a couple of examples that showcase what works well and what doesn’t:
Systems Analyst
Tech Solutions Inc. – Austin, TX
- Analyzed system requirements
- Documented processes and procedures
- Collaborated with team members on projects
- Troubleshot technical issues as they arose
- Lacks specific details about projects or systems worked on
- Bullet points do not highlight any measurable outcomes or successes
- Vague descriptions do not convey the job seeker's impact or expertise in the role
Systems Analyst
Tech Solutions Inc. – San Francisco, CA
March 2020 - Present
- Analyze and optimize system performance, achieving a 30% increase in processing speed through targeted improvements
- Develop and implement software solutions that reduced operational costs by $100,000 annually
- Collaborate with cross-functional teams to define project requirements, ensuring timely delivery of technology initiatives
- Uses effective action verbs to clearly convey the applicant's contributions
- Incorporates quantifiable results to highlight the effectiveness of their work
- Demonstrates relevant skills and teamwork essential for a systems analyst role
While your resume summary and work experience are important, don’t overlook the other sections that also require careful formatting. To ensure every part of your resume stands out, refer to our complete guide on how to write a resume.
Top Skills to Include on Your Resume
Including a skills section on your resume is important for demonstrating your qualifications at a glance. It allows potential employers to quickly identify if you possess the technical skills needed for the role of a systems analyst.
Be sure to include a mix of hard and soft skills to make your resume stronger. Highlight technical abilities with SQL, data modeling software, and project management tools like JIRA or Trello, along with analytical and organizational skills that support effective project execution and data-driven decision-making.
Soft skills, like problem-solving, teamwork, and communication, facilitate collaboration with stakeholders and ensure successful project outcomes.
When selecting the resume skills to include in your resume, it's important to align them with what employers expect from ideal job seekers. Many organizations use automated systems to filter out applicants who lack essential skills, so ensuring a match is important for getting noticed.
To effectively highlight your qualifications, carefully review job postings related to your desired position. These listings often reveal which specific skills are most valued, helping you tailor your resume to meet both recruiter and ATS requirements.
Pro Tip
10 skills that appear on successful systems analyst resumes
Highlighting essential skills on your resume can significantly increase your chances of catching the attention of recruiters for systems analyst positions. You can see these in-demand skills reflected in our resume examples, allowing you to apply with confidence knowing you present a professional image.
Here are 10 skills you should consider including in your resume if they fit your qualifications and role requirements:
Analytical thinking
Problem-solving
Attention to detail
Communication
Technical skill
Project management
Data analysis
Requirements gathering
User experience understanding
Agile methodology
Based on analysis of 5,000+ data systems administration professional resumes from 2023-2024
Resume Format Examples
Selecting the appropriate resume format is important for a systems analyst as it showcases your technical expertise, relevant experiences, and career growth in a clear and strong manner.
Functional
Focuses on skills rather than previous jobs
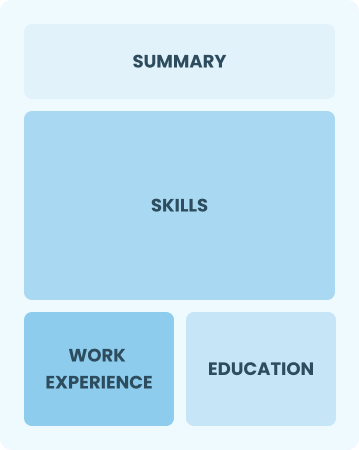
Best for:
Recent graduates and career changers with up to two years of experience
Combination
Balances skills and work history equally
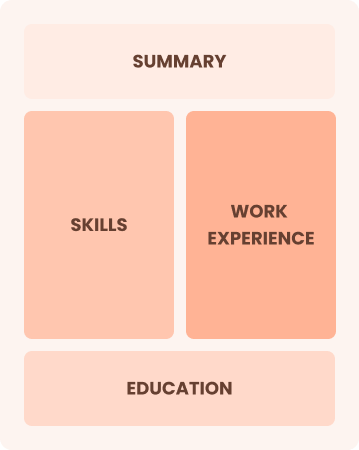
Best for:
Mid-career professionals focused on demonstrating key skills and growth potential
Chronological
Emphasizes work history in reverse order

Best for:
Seasoned analysts excelling in strategic solutions and team leadership
Systems Analyst Salaries in the Highest-Paid States
Our systems analyst salary data is based on figures from the U.S. Bureau of Labor Statistics (BLS), the authoritative source for employment trends and wage information nationwide.
Whether you're entering the workforce or considering a move to a new city or state, this data can help you gauge what fair compensation looks like for systems analysts in your desired area.
Frequently Asked Questions
Should I include a cover letter with my systems analyst resume?
Absolutely, including a cover letter is essential for making a strong impression on employers. A well-crafted cover letter highlights your skills and passion for the position, setting you apart from other applicants. If you need assistance in writing one, explore our comprehensive guide on how to write a cover letter or use our Cover Letter Generator to simplify the process and create an effective letter quickly.
Can I use a resume if I’m applying internationally, or do I need a CV?
A CV is often required for international job applications, especially in Europe and Asia, where it provides a comprehensive overview of your professional history. To assist with how to write a CV and formatting, explore our resources that offer CV examples and tips tailored to global standards.
What soft skills are important for systems analysts?
Soft skills like communication, problem-solving, and teamwork are essential for systems analysts. These interpersonal skills foster collaboration with stakeholders and help translate technical requirements into effective solutions, ensuring projects run smoothly and meet user needs.
I’m transitioning from another field. How should I highlight my experience?
Highlight your transferable skills such as analytical thinking, project management, and communication from previous roles. These abilities showcase your potential to thrive as a systems analyst, even if you lack direct experience in the field. Provide specific examples that connect your past successes to the responsibilities of the role, demonstrating your readiness to add value.
How should I format a cover letter for a systems analyst job?
To format a cover letter, start with your contact details at the top. Follow this by including a professional greeting and a compelling opening statement that captures the reader's attention. Share specific examples of your qualifications relevant to systems analyst roles, making sure you match your skills to the job requirements. Conclude with a strong call to action that invites further discussion.
How do I add my resume to LinkedIn?
To boost your resume's visibility on LinkedIn, you should add your resume to LinkedIn directly to your profile or emphasize key skills and experiences in the "About" and "Experience" sections. This strategy makes it easier for recruiters and hiring managers to find qualified systems analysts, improving your chances of being noticed for relevant opportunities.







