Hard skills are technical abilities like risk assessment, incident response planning, and knowledge of security systems that a security manager should highlight.
Popular Security Manager Resume Examples
Check out our top security manager resume examples that emphasize critical skills like risk assessment, team leadership, and incident response. These samples demonstrate how to effectively showcase your experience to potential employers.
Ready to build your ideal resume? Our Resume Builder offers user-friendly templates specifically designed for security professionals, helping you make a lasting impression.
Recommended
Security manager resume
The resume’s clean layout and use of resume fonts improve readability, allowing the applicant's qualifications to shine through. These design elements show attention to professionalism, which is important for making a strong impression in the security management field.
Security supervisor resume
This resume effectively integrates critical skills like security management and emergency response with substantial work experience. By showcasing these abilities alongside relevant job history, employers can clearly assess the applicant's competence in improving safety protocols and leading security teams.
Director of security resume
This resume showcases a clean layout with bullet points that effectively summarize the applicant's strong achievements in security management. The use of ample white space and organized sections allows hiring managers to quickly identify key contributions, making it easy to appreciate the applicant's qualifications at a glance.
Resume Template—Easy to Copy & Paste
Min Park
Crestwood, KY 40017
(555)555-5555
Min.Park@example.com
Professional Summary
Proactive Security Manager with 8+ years of experience in risk assessment, incident management, and robust surveillance solutions, increasing efficiency and reducing breaches by over 35%. Proven track record in leading and training teams while leveraging advanced security protocols to ensure asset protection.
Work History
Security Manager
Summit Security Services - Crestwood, KY
October 2022 - November 2025
- Designed security protocols, reducing breaches by 35%
- Managed a team of 15 personnel ensuring 100% compliance
- Implemented new surveillance tools saving 20,000 annually
Assistant Security Director
Pinnacle Protection Systems - Crestwood, KY
June 2018 - September 2022
- Led staff training programs with 90% effectiveness improvement
- Analyzed and mitigated risks, lowering incidents by 25%
- Collaborated with executives, enhancing safety measures by 40%
Security Specialist
SafeGuard Solutions - Crestwood, KY
December 2015 - May 2018
- Monitored systems ensuring 98% asset protection accuracy
- Investigated security breaches achieving 100% resolutions
- Coordinated access protocols resulting in a 20% efficiency gain
Languages
- Spanish - Beginner (A1)
- French - Beginner (A1)
- German - Beginner (A1)
Skills
- Access control management
- Incident management
- Risk assessment
- Conflict resolution
- Surveillance technology
- Crisis response planning
- Employee training programs
- Emergency preparedness
Certifications
- Certified Protection Professional (CPP) - ASIS International
- Security Risk Assessment Certified - International Association of Security Professionals
Education
Master of Science Security Management
University of Colorado Denver Denver, Colorado
May 2015
Bachelor of Science Criminal Justice
California State University Los Angeles, California
May 2013
How to Write a Security Manager Resume Summary
Your resume summary is the first thing employers will notice, so it’s important to make a lasting impression that showcases your qualifications as a security manager. This section provides an opportunity to highlight your expertise in risk management, team leadership, and incident response.
As a security manager, you should focus on demonstrating your ability to protect assets and ensure safety protocols are upheld. Emphasize your strategic thinking skills and experience in developing security policies.
To help clarify what works effectively in this section, we’ll provide some examples of strong resume summaries for security managers:
I am a dedicated security manager with extensive experience in the field. I want to find a job where I can use my skills to help an organization succeed. A position that allows for personal growth and development in a supportive environment is what I’m looking for. I believe I could be a great asset to your team if given the chance.
- Lacks specific examples of skills or accomplishments, leading to vagueness
- Emphasizes what the job seeker seeks rather than highlighting their contributions
- Uses generic language that does not differentiate the job seeker from others in similar roles
Result-driven security manager with 8 years of experience in corporate and retail settings, adept at risk assessment and crisis management. Successfully reduced security incidents by 30% through implementation of advanced surveillance systems and staff training programs. Proficient in access control technologies, emergency response planning, and leading cross-functional teams to improve overall security posture.
- Begins with specific years of experience and diverse industry exposure
- Highlights a quantifiable achievement that shows significant improvement in security measures
- Mentions technical skills and leadership abilities important for a security management role
Pro Tip
Showcasing Your Work Experience
The work experience section is important for your resume as a security manager, where you will provide the bulk of your content. Quality resume templates always emphasize this important area to highlight your relevant experience.
This section should be organized in reverse-chronological order, detailing your previous positions. Use bullet points to succinctly describe your key achievements and contributions in each role.
To assist you further, we will showcase a couple of examples that illustrate effective entries for a security manager's work history. These examples will clarify what resonates positively and what may fall short:
Security Manager
SafeGuard Security Inc. – Austin, TX
- Monitored security systems
- Led a team of guards
- Wrote reports and maintained logs
- Responded to incidents as needed
- Lacks specific details about responsibilities and achievements
- Bullet points are overly simplistic and do not highlight key skills
- Does not provide any measurable outcomes or impacts of the work done
Security Manager
Global Tech Solutions – New York, NY
March 2020 - Current
- Develop and implement comprehensive security protocols that decreased incidents by 30% over two years
- Lead a team of 15 security personnel, improving training programs which improved response times to emergencies by 40%
- Conduct regular risk assessments and audits, successfully identifying vulnerabilities that led to the implementation of critical infrastructure upgrades
- Uses strong action verbs to clearly convey achievements
- Incorporates specific metrics that demonstrate significant improvements in safety and efficiency
- Highlights essential skills relevant to security management through detailed accomplishments
While your resume summary and work experience are important elements, don’t overlook the importance of other sections. Each part plays a role in showcasing your qualifications effectively. For detailed guidance, be sure to check out our complete guide on how to write a resume.
Top Skills to Include on Your Resume
A skills section is essential for any resume, as it quickly shows employers that you have the necessary qualifications for the role. By clearly outlining your abilities, you can make a strong first impression and increase your chances of landing an interview.
For a security manager, emphasize both technical skills and interpersonal abilities. Highlight proficiency with threat detection software, incident response systems, and knowledge of security protocols to demonstrate your capability in managing safety and leading security operations effectively.
Soft skills include strong communication, problem-solving, and leadership qualities essential for effective teamwork and fostering a culture of safety within the organization.
When selecting your resume skills, aligning them with what employers expect from applicants is important. Many organizations use automated systems to screen resumes, so including the right skills can significantly impact your chances of getting noticed.
To highlight the most relevant skills, carefully review job postings related to your target position. These listings often reveal which qualifications are essential for both recruiters and ATS systems, guiding you on what to emphasize in your application.
Pro Tip
10 skills that appear on successful security manager resumes
Highlighting essential skills on your resume significantly increases your chances of attracting recruiters' attention. These high-demand abilities are showcased in our resume examples, allowing you to approach job applications with confidence and professionalism.
By the way, consider incorporating relevant skills from the following list that align with your experience and job requirements:
Risk management
Team leadership
Crisis response
Communication skills
Analytical thinking
Incident investigation
Compliance knowledge
Security technology skill
Training and development
Attention to detail
Based on analysis of 5,000+ management professional resumes from 2023-2024
Resume Format Examples
Choosing the suitable resume format is important because it effectively highlights your relevant skills, experience, and career progression, making it easier for potential employers to quickly grasp your qualifications.
Functional
Focuses on skills rather than previous jobs
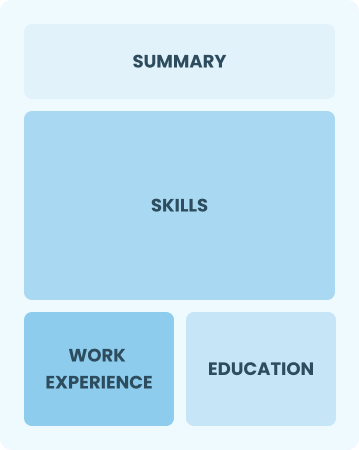
Best for:
Recent graduates and career changers with little to no experience in security management
Combination
Balances skills and work history equally
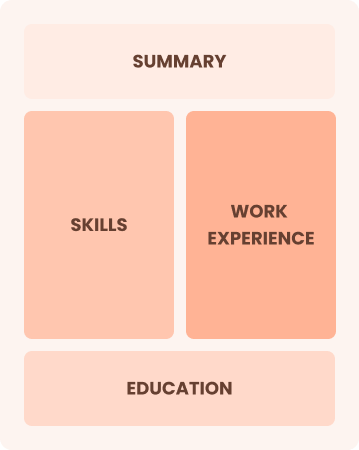
Best for:
Mid-career professionals focused on showcasing their skills and growth potential
Chronological
Emphasizes work history in reverse order

Best for:
Experienced leaders driving strategic security initiatives and risk management
Frequently Asked Questions
Should I include a cover letter with my security manager resume?
Absolutely, including a cover letter is essential for making your application memorable. It allows you to highlight your qualifications and demonstrate genuine interest in the position. If you're looking for tips on crafting an effective cover letter, explore our comprehensive guide on how to write a cover letter or use the Cover Letter Generator to simplify the process and tailor your message effectively.
Can I use a resume if I’m applying internationally, or do I need a CV?
When applying for jobs outside the U.S., use a CV instead of a resume, as many countries prefer this format. To assist you, we offer comprehensive resources and CV examples that adhere to international standards. Additionally, you can find guidance on how to write a CV effectively.
What soft skills are important for security managers?
Interpersonal skills, leadership, problem-solving, and communication are essential for a security manager. These skills enable effective coordination with teams, ensure clear communication of protocols, and foster trust among colleagues, ultimately improving overall security operations.
I’m transitioning from another field. How should I highlight my experience?
Highlight your transferable skills such as leadership, communication, and crisis management when applying for security manager roles. Even if your background is outside of security, these abilities are important. Use concrete examples from past experiences to show how you can effectively handle security challenges and improve safety measures in any environment.
Where can I find inspiration for writing my cover letter as a security manager?
For aspiring security managers, exploring professional cover letter examples can be incredibly beneficial. These samples provide valuable insights into effective content ideas, formatting techniques, and ways to showcase your qualifications. They serve as a great resource to help you craft an application that compellingly stands out.
How do I write a resume with no experience?
Crafting a resume with no experience for a security manager role can be achieved by highlighting relevant coursework, leadership roles in clubs, certifications, and skills like problem-solving and attention to detail. Emphasize your readiness to protect assets and ensure safety, showcasing your potential to impress employers despite limited formal work history.







