Hard skills cover critical abilities like network security, threat analysis, and vulnerability assessment. These skills are essential for professionals in cyber security to protect information systems.
Popular Cyber Security Resume Examples
Check out our top cyber security resume examples that emphasize critical skills such as risk assessment, threat analysis, and incident response. These examples will help you effectively showcase your accomplishments to potential employers.
Ready to build your standout resume? Our Resume Builder offers user-friendly templates specifically designed for professionals in the cyber security field, making your job search easier.
Recommended
Entry-level cyber security resume
This entry-level resume for cyber security effectively highlights the job seeker's technical skills and accomplishments gained through academic and professional experiences. New professionals in this field must demonstrate their understanding of cybersecurity principles and relevant certifications, showcasing their ability to contribute to organizational safety even with limited work history.
Mid-career cyber security resume
This resume effectively showcases the applicant's comprehensive experience in cyber security, demonstrating a proven track record of threat reduction and leadership in complex projects. The qualifications highlight their readiness for advanced roles and commitment to ongoing professional development in a rapidly evolving field.
Experienced cyber security resume
The work history section highlights the applicant's extensive experience in cybersecurity, showcasing impressive achievements such as a 40% reduction in security breaches and managing 60 cyber threats monthly. The concise bullet points improve readability, making it easy for potential employers to recognize key accomplishments quickly.
Resume Template—Easy to Copy & Paste
Ming Huang
Minneapolis, MN 55411
(555)555-5555
Ming.Huang@example.com
Professional Summary
Cyber Security Specialist with 9 years of experience in enhancing information security, risk management, and threat analysis. Proven track record of reducing data breaches by 30% and improving network architecture. Equipped with strong skills in network defense and cryptography to secure sensitive information.
Work History
Cyber Security Specialist
SecureTech Solutions - Minneapolis, MN
May 2022 - January 2026
- Reduced data breaches by 30% annually
- Led a team of 5 to improve system integrity
- Implemented new security protocols
Information Security Analyst
DataGuard Inc. - Minneapolis, MN
July 2017 - April 2022
- Enhanced firewall efficiency by 40%
- Conducted risk assessments biannually
- Managed security audits for top clients
Network Security Engineer
NetSecure Systems - Minneapolis, MN
May 2013 - June 2017
- Improved network uptime by 25%
- Designed secure network architectures
- Trained staff in security awareness
Languages
- Spanish - Beginner (A1)
- German - Intermediate (B1)
- Mandarin - Beginner (A1)
Skills
- Threat Analysis
- Network Defense
- Incident Response
- Risk Management
- Cryptography
- Firewalls and VPNs
- Penetration Testing
- Security Protocols
Certifications
- Certified Information Systems Security Professional (CISSP) - ISC²
- Certified Ethical Hacker (CEH) - EC-Council
Education
Master of Science Cyber Security
Stanford University Stanford, California
June 2013
Bachelor of Science Computer Science
University of California, Berkeley Berkeley, California
June 2011
How to Write a Cyber Security Resume Summary
Your resume summary is your chance to make a powerful first impression, as it’s the first section hiring managers will see. This brief snapshot should capture your strengths and set the tone for your application.
In the field of cyber security, it’s essential to highlight your technical skills, problem-solving abilities, and experience with risk management. Showcasing these qualifications will demonstrate your readiness to tackle the challenges in this dynamic industry.
To further illustrate what makes an effective resume summary in cyber security, here are some examples that highlight both successful approaches and common pitfalls:
I am a dedicated cyber security professional with many years of experience. I want a position where I can use my skills to help the company succeed. A job that offers flexibility and room for advancement would be great for me. I believe I can contribute positively if given the chance.
- Lacks specific details about relevant skills or achievements in cyber security, making it vague
- Overuses personal language, which detracts from professionalism and could be seen as filler
- Emphasizes personal desires instead of highlighting how the applicant can add value to potential employers
Results-driven cybersecurity analyst with 7+ years of experience safeguarding organizational assets and mitigating threats. Achieved a 40% decrease in security breaches through the implementation of proactive threat detection systems and employee training programs. Proficient in risk assessment, incident response, and various security technologies including firewalls and intrusion detection systems.
- Begins with clear years of experience and specific focus area in cybersecurity
- Highlights quantifiable achievement that illustrates significant impact on organizational security
- Showcases relevant technical skills that are critical for addressing modern cybersecurity challenges
Pro Tip
Showcasing Your Work Experience
The work experience section is the cornerstone of your resume in cyber security. This area will contain the majority of your content, and resume templates always emphasize its importance.
In this section, list your previous positions in reverse-chronological order. Use bullet points to succinctly describe accomplishments and skills applied in each role, showcasing the impact on security measures.
To guide you further, we’ll present a couple of examples that illustrate strong work history entries for cyber security professionals. These examples will highlight effective strategies and common pitfalls to avoid.
Cyber Security Analyst
Tech Solutions Inc. – San Francisco, CA
- Monitored network security.
- Responded to security incidents.
- Reviewed system logs and reports.
- Assisted in implementing security measures.
- Lacks specific details about the nature of incidents handled
- Bullet points do not highlight any measurable impact or improvements made
- Focuses on routine tasks instead of showcasing unique skills or achievements
Cyber Security Analyst
Tech Solutions Inc. – San Francisco, CA
March 2020 - Current
- Conduct regular security assessments and vulnerability scans, identifying and mitigating risks that reduced potential breaches by 40%.
- Develop and implement incident response plans, leading to a 30% decrease in response time during security incidents.
- Collaborate with IT teams to improve network security protocols, improving overall system integrity and compliance with industry standards.
- Uses powerful action verbs at the beginning of each bullet point to demonstrate the applicant's contributions
- Incorporates specific metrics that quantify achievements, providing concrete evidence of effectiveness
- Highlights relevant skills such as risk management and collaboration that are critical to the cyber security field
While your resume summary and work experience are important, don’t overlook other sections that contribute to a strong application. For detailed advice on perfecting every part of your resume, be sure to check out our comprehensive guide on how to write a resume.
Top Skills to Include on Your Resume
A skills section is vital on your resume as it provides a clear, concise overview of your qualifications and expertise. This allows job seekers to present their most relevant abilities while giving employers a quick reference point for assessing applicant suitability.
Add both hard and soft skills to create a well-rounded resume.
Soft skills are essential for cyber security professionals, as they improve teamwork, communication, and problem-solving abilities. These skills foster a collaborative environment to effectively combat security threats.
Selecting the right resume skills is important for aligning with what employers seek in potential job seekers. Many organizations use automated systems to filter applicants who lack essential abilities relevant to the job.
To improve your chances of getting noticed, carefully review job postings for insights on which capabilities are most valued. Highlighting these in your resume can help engage both recruiters and ATS systems, increasing your opportunities for success.
Pro Tip
10 skills that appear on successful cyber security resumes
Highlighting sought-after skills in your resume can significantly increase your chances of catching a recruiter's eye. These skills are often featured in our resume examples, giving you the confidence to apply with a polished presentation.
By the way, make sure to incorporate relevant skills from the following list that align with your experience and job requirements:
Network security
Incident response
Risk assessment
Malware analysis
Firewalls and VPNs
Encryption techniques
Security audits
Cloud security
Compliance knowledge
Vulnerability management
Based on analysis of 5,000+ safety security professional resumes from 2023-2024
Resume Format Examples
Choosing the right resume format is important in cyber security because it highlights your technical expertise, relevant experience, and career growth clearly and appealingly.
Functional
Focuses on skills rather than previous jobs
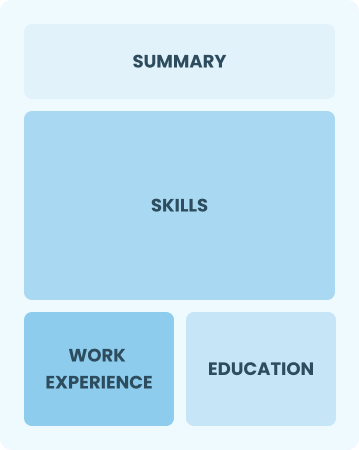
Best for:
Recent graduates and career changers with limited experience in cyber security
Combination
Balances skills and work history equally
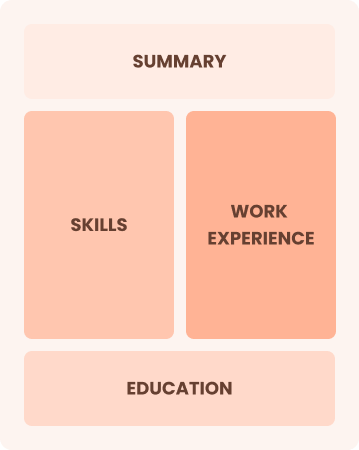
Best for:
Mid-career professionals focused on demonstrating their skills and growth potential
Chronological
Emphasizes work history in reverse order

Best for:
Experienced leaders excelling in advanced cyber security strategies
Frequently Asked Questions
Should I include a cover letter with my cyber security resume?
Absolutely. A cover letter can significantly improve your application by showcasing your personality and enthusiasm for the position. It allows you to highlight relevant experiences and explain how they align with the job requirements. For tips on crafting an effective cover letter, explore our how to write a cover letter guide. You can also use our Cover Letter Generator to simplify the process.
Can I use a resume if I’m applying internationally, or do I need a CV?
When applying for jobs outside the U.S., use a CV instead of a resume, as many countries prefer this format. To assist you in crafting an effective CV, explore our comprehensive resources that provide CV examples and guidelines on how to write a CV, including proper formatting and creation techniques.
What soft skills are important for cyber securitys?
Soft skills like problem-solving, communication, and interpersonal skills are essential in cyber security. These abilities help professionals work well with teams and convey complex information clearly, which is important for identifying vulnerabilities and responding to threats efficiently.
I’m transitioning from another field. How should I highlight my experience?
Highlight your transferable skills such as analytical thinking, teamwork, and adaptability from prior roles. These attributes illustrate your potential to excel in cyber security, even if you're new to the field. Share specific instances where you've successfully solved problems or managed projects to demonstrate how your experience aligns with key responsibilities in this domain.
Where can I find inspiration for writing my cover letter as a cyber security?
When crafting your cover letter for cyber security roles, consider exploring cover letter examples. These samples offer inspiration for content ideas, formatting tips, and effective ways to showcase your qualifications. A well-structured cover letter can set you apart in this competitive field.
Should I include a personal mission statement on my cyber security resume?
Including a personal mission statement on your resume is highly recommended. It effectively showcases your core values and career aspirations, making it especially powerful for companies that prioritize cultural fit and mission-driven work environments.







