Hard skills are technical, measurable abilities like data analysis, process optimization, and project management that ensure efficient business operations.
Popular Business Operations Resume Examples
Check out our top business operations resume examples that emphasize key skills like strategic planning, process optimization, and team leadership. These examples are designed to help you effectively showcase your achievements in this dynamic field.
Ready to build your ideal resume? Our Resume Builder offers user-friendly templates specifically crafted for professionals in business operations, making your application stand out.
Recommended
Operations analyst resume
The resume features a modern layout with consistent resume fonts that improve readability. These design elements not only create a professional appearance but also effectively highlight the applicant's achievements and skills, making a lasting impression on potential employers.
Business operations specialist resume
This resume effectively combines key skills such as project management and operations optimization with relevant work experience. By showcasing these abilities alongside a solid track record in boosting efficiency and reducing costs, employers can clearly see the applicant's potential contributions to their organization.
Operations coordinator resume
This resume showcases extensive experience through well-organized bullet points that clearly outline achievements, making it simple for hiring managers to identify key qualifications. The effective use of headings and strategic spacing ensures that critical details stand out while maintaining a clean and professional appearance.
Resume Template—Easy to Copy & Paste
Mason Hughes
Eastside, WA 98004
(555)555-5555
Mason.Hughes@example.com
Professional Summary
Experienced Business Operations professional with expertise in workflow optimization, budget management, and cross-functional team leadership. Proven ability to deliver 25%+ efficiency gains and drive 95%+ project completion success. Adept at transforming processes to support long-term business growth.
Work History
Business Operations
Strategic Solutions Group - Eastside, WA
January 2023 - October 2025
- Optimized workflows, increasing efficiency by 25%
- Managed budgets of up to M annually, reducing costs by 10%
- Led cross-functional teams to achieve 95% project completion rate
Operations Analyst
BlueWave Consulting - Tacoma, WA
June 2020 - December 2022
- Streamlined data reporting, reducing lead time by 30%
- Analyzed KPIs to support decisions, influencing 15% revenue growth
- Implemented tools reducing manual workload by 20%
Business Coordinator
Pinnacle Operations - Silverlake, WA
October 2018 - May 2020
- Coordinated business processes boosting delivery time by 12%
- Monitored budgets ensuring 98% adherence to financial planning
- Generated reports driving 20% improvement in operational insights
Skills
- Process Optimization
- Budget Management
- Cross-Functional Team Leadership
- Data Analysis and Reporting
- Strategic Planning
- KPI Monitoring
- Workflow Automation
- Project Management
Education
Master of Business Administration Business Administration
Harvard Business School Boston, Massachusetts
May 2018
Bachelor of Science Business Administration
University of California, Berkeley Berkeley, California
May 2016
Certifications
- Certified Business Operations Professional - Global Operations Institute
- Lean Six Sigma Green Belt - International Lean Institute
Languages
- Spanish - Beginner (A1)
- French - Beginner (A1)
- German - Beginner (A1)
How to Write a Business Operations Resume Summary
Your resume summary is the first impression hiring managers will have of you, making it important to present yourself effectively. As a business operations professional, your summary should emphasize skills in efficiency, strategic planning, and problem-solving.
Highlight your experience in optimizing processes and driving organizational success. This section should reflect your ability to improve productivity and navigate challenges within a business environment.
To illustrate what works well in a resume summary for this role, we’ll look at some examples that showcase effective strategies and common pitfalls:
I have worked in business operations for many years and have a lot of skills that I can use. I am looking for a job where I can do well and help the company succeed. A good work environment with chances for advancement is important to me. I believe I would be a great addition if given the chance.
- Lacks specific details about the job seeker's achievements or unique skills, making it generic
- Overuses personal pronouns which dilute impact and make it seem less professional
- Emphasizes what the applicant desires from the role instead of illustrating how they can contribute to the employer's success
Results-driven business operations manager with over 7 years of experience in streamlining processes and improving operational efficiency. Achieved a 20% reduction in operational costs through strategic resource allocation and process optimization initiatives. Proficient in project management, data analysis, and using ERP software to drive productivity improvements across departments.
- Begins with specific experience level and focus on business operations
- Includes quantifiable achievement that highlights tangible impact on cost savings
- Showcases relevant technical skills and competencies that are valuable to employers
Pro Tip
Showcasing Your Work Experience
The work experience section is important for your resume in business operations, as this is where the bulk of your content will be concentrated. Good resume templates always emphasize this important section.
In this area, you should list your previous roles in reverse-chronological order, highlighting your progression. Use bullet points to detail your key achievements and contributions in each position.
To help you understand effective presentation, we’ll provide a couple of examples that illustrate what works well and what pitfalls to avoid:
Business Operations Manager
XYZ Corp – New York, NY
- Managed daily operations.
- Handled scheduling and inventory.
- Coordinated with teams for project delivery.
- Assisted in budget tracking and reporting.
- Lacks specific accomplishments or metrics to showcase impact
- Bullet points are overly simplistic and do not highlight leadership skills
- No mention of improvements made to processes or efficiency
Business Operations Manager
Innovate Corp – San Francisco, CA
March 2018 - Present
- Streamlined operational processes, reducing overhead costs by 15% annually through effective resource management.
- Led cross-functional teams to drive strategic initiatives, resulting in a 30% increase in productivity over two years.
- Implemented data-driven decision-making frameworks that improved project outcomes and improved customer satisfaction ratings by 20%.
- Starts with effective action verbs to clearly demonstrate achievements
- Incorporates specific percentages to quantify success and impact
- Highlights relevant skills such as resource management and strategic planning
While your resume summary and work experience are important parts of your application, don't overlook other sections that also deserve careful attention. For additional guidance on how to write a resume effectively, be sure to explore our detailed guide on crafting an effective resume.
Top Skills to Include on Your Resume
A skills section is key for any resume because it quickly showcases your qualifications to potential employers. This area highlights your expertise, making it easier for hiring managers to see how you fit the role.
For business operations professionals, emphasize both technical skills and soft skills. Highlight specific tools like Microsoft Excel, project management software such as Asana, and data analysis systems to demonstrate your capability in managing various tasks efficiently.
Soft skills include interpersonal qualities such as communication, problem-solving, and adaptability that foster collaboration and drive success in a dynamic work environment.
Selecting the right resume skills is important for aligning with what employers expect from job seekers. Many companies use automated systems to filter out applicants who lack essential skills, making it critical to highlight your qualifications effectively.
To determine which skills to emphasize, carefully review job postings for specific requirements and desired attributes. This strategy will not only help you appeal to recruiters but also ensure your resume meets the criteria set by ATS systems.
Pro Tip
10 skills that appear on successful business operations resumes
To capture the attention of recruiters, it's essential to highlight high-demand skills relevant to business operations roles. You can find these skills effectively showcased in our resume examples, giving you the advantage of a well-crafted professional profile.
If you have experience that aligns with these key competencies, consider adding them to your resume:
Analytical thinking
Project management
Leadership
Process improvement
Financial acumen
Data analysis
Team collaboration
Strategic planning
Adaptability
Communication skills
Based on analysis of 5,000+ business operations professional resumes from 2023-2024
Resume Format Examples
Selecting the appropriate resume format is important for showcasing your business operations expertise, as it emphasizes your key skills and relevant experience while clearly mapping your career growth.
Functional
Focuses on skills rather than previous jobs
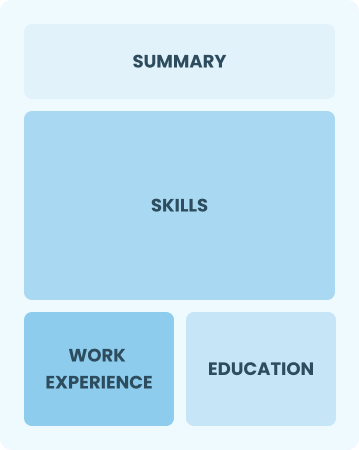
Best for:
Recent graduates and career changers with up to two years of experience
Combination
Balances skills and work history equally
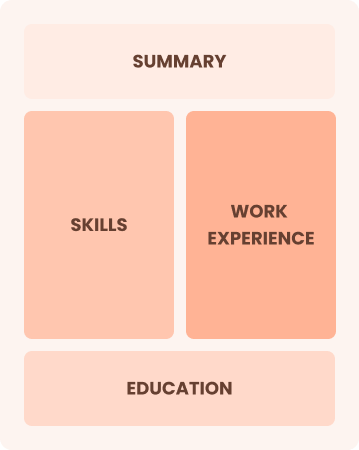
Best for:
Mid-career professionals eager to demonstrate their skills and advance their careers
Chronological
Emphasizes work history in reverse order

Best for:
Seasoned leaders driving strategic initiatives in business operations
Business Operations Salaries in Popular States
Our business operations salary data is based on figures from the U.S. Bureau of Labor Statistics (BLS), the authoritative source for employment trends and wage information nationwide.
Whether you're entering the workforce or considering a move to a new city or state, this data can help you gauge what fair compensation looks like for business operationss in your desired area.
Frequently Asked Questions
Should I include a cover letter with my business operations resume?
Absolutely! Including a cover letter can significantly improve your application by showcasing your passion and qualifications for the position. It provides an opportunity to explain how your skills align with the company's needs. To get started, consider checking our comprehensive guide on how to write a cover letter or use our Cover Letter Generator to craft one quickly and easily.
Can I use a resume if I’m applying internationally, or do I need a CV?
When applying for jobs outside the U.S., use a CV instead of a resume. A CV offers a comprehensive overview of your academic and professional history, which is often preferred in many countries. Explore our resources on how to write a CV and check out various CV examples to improve your applications.
What soft skills are important for business operationss?
Soft skills such as communication, problem-solving, and adaptability are essential in business operations. These interpersonal skills foster effective collaboration among team members and improve relationships with clients, leading to smoother processes and improved overall efficiency.
I’m transitioning from another field. How should I highlight my experience?
Highlight your transferable skills such as project management, analytical thinking, and communication. These abilities demonstrate your readiness to excel in business operations roles, even if your prior experience is in a different sector. Use concrete examples of past accomplishments that directly connect to the responsibilities of the position you’re aiming for.
Where can I find inspiration for writing my cover letter as a business operations?
For job seekers in business operations, exploring cover letter examples can be invaluable. These samples offer insights into effective content ideas, formatting tips, and strategies for showcasing your qualifications. Use them as a guide to craft compelling application materials that stand out to employers.
Should I include a personal mission statement on my business operations resume?
Yes, incorporating a personal mission statement in your resume is advisable. It effectively highlights your core values and career aspirations. This strategy works particularly well when targeting companies that emphasize alignment with their mission or demonstrate a strong focus on organizational culture.







