Hard skills are technical, measurable abilities such as criminal investigation techniques, firearms skills, and knowledge of legal statutes.
Popular Law Enforcement Resume Examples
Discover our top law enforcement resume examples that emphasize skills such as investigation techniques, community policing, and crisis management. These examples will help you effectively showcase your accomplishments to potential employers.
Ready to build your own impressive resume? Our Resume Builder offers user-friendly templates specifically designed for professionals in law enforcement.
Recommended
Police officer resume
The resume showcases a structured layout with clear headings and bullet points, improving readability for hiring managers. The use of resume fonts paired with consistent formatting highlights the job seeker's attention to detail, helping their qualifications stand out effectively in a competitive field.
Sheriff's deputy resume
This resume effectively balances critical skills like crime prevention and investigation techniques with extensive work experience in law enforcement. By demonstrating these abilities alongside practical achievements, employers can assess the job seeker's effectiveness in addressing community safety and operational challenges.
State trooper resume
This resume effectively uses bullet points to clearly present extensive law enforcement experience, allowing hiring managers to quickly grasp key achievements. The use of strategic spacing and organized sections improves readability, making it easier to identify qualifications and contributions at a glance.
Resume Template—Easy to Copy & Paste
Aya Lee
Maplewood, NJ 07047
(555)555-5555
Aya.Lee@example.com
Professional Summary
Accomplished Law Enforcement professional with 7 years of experience in public safety and crime prevention. Proven track record of reducing crime rates, managing complex investigations, and fostering community trust. Expertise in emergency response planning, surveillance systems management, and conflict mediation.
Work History
Law Enforcement Officer
Cityline Police Department - Maplewood, NJ
November 2020 - November 2025
- Reduced crime rate by 18% through community engagement
- Conducted 200+ investigations, leading to successful case closures
- Implemented safety protocols, increasing public confidence by 12%
Public Safety Enforcer
Metro Guard Services - Newark, NJ
November 2016 - November 2020
- Managed patrol routes, ensuring 98% coverage of safety zones
- Executed emergency plans, reducing response time to under 5 mins
- Trained 30+ recruits on safety operations and communication skills
Security Compliance Specialist
Legacy Security Solutions - Jersey City, NJ
November 2013 - November 2016
- Monitored facilities to achieve 100% adherence to security policies
- Facilitated 15+ risk mitigation workshops for staff members
- Drafted reports documenting 150+ security incidents yearly
Skills
- Community Policing
- Crime Prevention Strategies
- Investigative Techniques
- Emergency Response Planning
- Conflict Mediation
- Surveillance Systems Management
- Report Writing & Documentation
- Criminal Law Knowledge
Certifications
- Certified Law Enforcement Officer - National Law Enforcement Certification Board
- Advanced Crime Scene Management - American Police Academy
- Tactical Training Expert - Defense Training Institute
Education
Master's Degree Criminal Justice
National University of Criminal Justice Indianapolis, Indiana
May 2012
Bachelor's Degree Law Enforcement
Midwest State University Des Moines, Iowa
May 2010
Languages
- Spanish - Beginner (A1)
- French - Beginner (A1)
- Mandarin - Intermediate (B1)
How to Write a Law Enforcement Resume Summary
Your resume summary is important as it’s the first thing employers see, making a strong impression that can set you apart from other job seekers. As a law enforcement professional, you should emphasize your commitment to public safety, problem-solving abilities, and any specialized training that showcases your qualifications.
Highlighting your experience in community engagement, crisis resolution, and legal knowledge will strengthen your position. These elements demonstrate not only your capabilities but also your dedication to maintaining peace and order.
To assist you in crafting an effective summary, the following examples will illustrate what works well and what doesn’t:
I am a dedicated law enforcement officer with several years of service and diverse experience. I seek a position that allows me to apply my skills while also providing room for advancement. I believe I can positively impact the department if given the chance.
- Lacks specific achievements or examples of how the applicant has made an impact in previous roles
- Relies on generic statements about career aspirations rather than articulating unique contributions
- Emphasizes personal desires over what value the applicant brings to potential employers
Experienced law enforcement officer with over 6 years in community policing and crime prevention. Successfully decreased local crime rates by 20% through proactive engagement initiatives and collaboration with neighborhood organizations. Proficient in crisis intervention, investigative procedures, and using advanced technology for data analysis in criminal investigations.
- Starts with a clear indication of experience level and specific areas of expertise
- Highlights a quantifiable achievement that showcases a significant impact on community safety
- Mentions relevant skills that align with the demands of law enforcement roles
Pro Tip
Showcasing Your Work Experience
The work experience section is important for a law enforcement resume, as it contains the bulk of your content. Good resume templates always emphasize this section to highlight your professional journey.
This section should be organized in reverse-chronological order, detailing your previous positions. Use bullet points to clearly present your achievements and contributions in each role within law enforcement.
To better illustrate this, we’ll provide some examples that showcase effective work history entries for law enforcement professionals. These examples will help you discern what works well and what doesn't:
Police Officer
City Police Department – Anytown, USA
- Patrolled neighborhoods.
- Responded to calls for service.
- Wrote reports and interacted with the community.
- Handled various incidents as they arose.
- Lacks specific examples of achievements or impacts made in the role
- Bullet points are too general and do not showcase unique skills or contributions
- Does not mention any training, awards, or recognitions that demonstrate professional growth
Police Officer
City of Springfield Police Department – Springfield, IL
March 2018 - Current
- Conduct proactive patrols and community engagement initiatives, leading to a 15% decrease in local crime rates over two years.
- Respond to emergency calls and incidents, providing critical first response care that ensures public safety and minimizes harm.
- Collaborate with local organizations to facilitate educational programs on crime prevention, resulting in increased community awareness.
- Uses strong action verbs that clearly convey the officer’s contributions and impact
- Incorporates specific metrics, demonstrating measurable outcomes of actions taken
- Highlights relevant skills such as community engagement and emergency response essential for law enforcement roles
While your resume summary and work experience are critical components, don't overlook the importance of other sections. Each part contributes to showcasing your qualifications effectively. For detailed guidance, be sure to read our comprehensive guide on how to write a resume.
Top Skills to Include on Your Resume
A skills section is important on your resume as it allows you to quickly showcase your qualifications to potential employers. It provides a snapshot of your abilities, helping you stand out in a competitive job market.
For law enforcement roles, emphasize both technical skills and interpersonal skills. Highlight skills in tools like crime analysis software, report writing systems, and community policing techniques that demonstrate your capability to perform effectively in the field.
Soft skills include communication, problem-solving, and teamwork, which are essential for building trust within the community and effectively collaborating with colleagues in high-pressure situations.
When selecting your resume skills, it's important to align them with what employers are seeking. Many organizations use automated systems to screen job seekers, so it's essential that your skills meet the job requirements.
Reviewing job postings carefully can provide insights on which skills are emphasized, allowing you to effectively showcase your abilities. This practice will help tailor your resume to resonate with both recruiters and ATS systems alike.
Pro Tip
10 skills that appear on successful law enforcement resumes
Improving your resume by incorporating high-demand skills can significantly attract the attention of recruiters in law enforcement. You’ll discover these and other essential traits highlighted in our resume examples, allowing you to approach job applications with renewed confidence.
Here are 10 skills you should consider including in your resume if they align with your background and job specifications:
Analytical thinking
Conflict resolution
Strong communication
Attention to detail
Team collaboration
Crisis management
Physical fitness
Knowledge of legal procedures
Surveillance techniques
Report writing
Based on analysis of 5,000+ law enforcement professional resumes from 2023-2024
Resume Format Examples
Choosing the right resume format is important for law enforcement professionals as it clearly and effectively highlights essential skills, relevant experience, and career advancements.
Functional
Focuses on skills rather than previous jobs
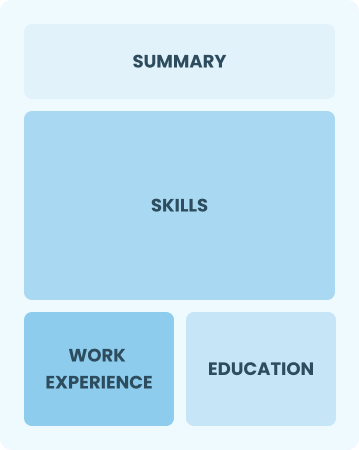
Best for:
Recent graduates and career changers with limited experience in law enforcement
Combination
Balances skills and work history equally
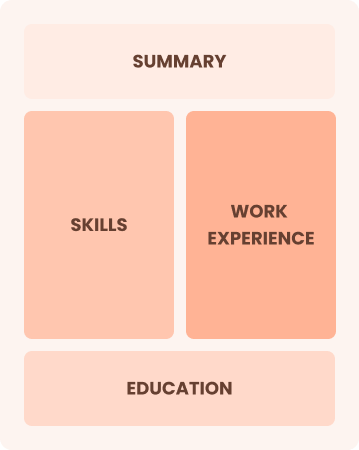
Best for:
Mid-career professionals focused on demonstrating their skills and growth potential
Chronological
Emphasizes work history in reverse order

Best for:
Best for experienced leaders in community safety and specialized investigations
Law Enforcement Salaries in the Highest-Paid States
Our law enforcement salary data is based on figures from the U.S. Bureau of Labor Statistics (BLS), the authoritative source for employment trends and wage information nationwide.
Whether you're entering the workforce or considering a move to a new city or state, this data can help you gauge what fair compensation looks like for law enforcement in your desired area.
Frequently Asked Questions
Should I include a cover letter with my law enforcement resume?
Certainly, adding a cover letter can greatly improve your application by demonstrating your qualifications and enthusiasm for the position. A well-crafted cover letter gives you the chance to explain how your skills match the job requirements. For assistance, our guide on how to write a cover letter is an excellent resource, or you can use our Cover Letter Generator for quick help.
Can I use a resume if I’m applying internationally, or do I need a CV?
When applying for jobs abroad, use a CV instead of a resume. A CV provides a comprehensive view of your academic and professional history, which is often preferred in international markets. Explore our guides on how to write a CV and check out various CV examples to create one that aligns with global expectations.
What soft skills are important for law enforcements?
Soft skills like communication, empathy, and conflict resolution are essential in law enforcement. These interpersonal skills foster trust and understanding between officers and the community, enabling effective collaboration and ensuring a safer environment for all.
I’m transitioning from another field. How should I highlight my experience?
Highlight your transferable skills such as communication, teamwork, and critical thinking from previous jobs. These abilities are important in law enforcement and illustrate your potential to excel despite limited direct experience. Provide concrete examples that align your past successes with the demands of the role to showcase how you can make a positive impact.
How do I write a resume with no experience?
If you’re entering law enforcement with limited experience, highlight relevant training, internships, or community involvement. For tips on crafting a resume with no experience, focus on skills like teamwork, problem-solving, and communication. Your dedication to serving the community can shine through your application. Remember, enthusiasm and a willingness to learn can make a strong impression on employers.
Should I include a personal mission statement on my law enforcement resume?
Yes, including a personal mission statement in your resume is recommended. It effectively showcases your values and aspirations, making it especially beneficial for law enforcement agencies that prioritize community service and integrity in their culture.







