Hard skills like strategic planning, budget management, and compliance with healthcare regulations are important for effectively overseeing operations.
Resume Template—Easy to Copy & Paste
Min Martinez
Cedar Valley, MN 55131
(555)555-5555
Min.Martinez@example.com
Skills
- Strategic Planning
- Project Management
- Budget Optimization
- Team Leadership
- Market Analysis
- Problem Solving
- Sales Growth
- Operational Efficiency
Languages
- Spanish - Beginner (A1)
- French - Beginner (A1)
- German - Intermediate (B1)
Professional Summary
Effective leader with 6 years experience in strategic roles. Increased productivity and sales while optimizing operations. Expertise in business strategy, project management.
Work History
Director
Strategic Solutions Inc. - Cedar Valley, MN
October 2023 - October 2025
- Optimized operations reducing costs by 20%
- Led team to increase productivity by 30%
- Implemented new strategy increasing market share
Senior Manager
Innovate Corp - Minneapolis, MN
October 2021 - September 2023
- Developed marketing campaign boosting sales 40%
- Managed budget saving company 200,000
- Expanded regional presence by securing 5 new clients
Project Lead
VisionTech Solutions - Cedar Valley, MN
October 2019 - September 2021
- Spearheaded project achieving goals ahead of schedule
- Collaborated with team to deliver high-quality outputs
- Enhanced product reliability reducing defects by 15%
Certifications
- Certified Project Director - Project Management Institute
- Strategic Leadership Certificate - Harvard Business School
Education
Master's Business Administration
Harvard University Cambridge, Massachusetts
May 2019
Bachelor's Management
University of Illinois Urbana, Illinois
May 2017
How to Write a Director Resume Summary
Your resume summary is the first impression you make on hiring managers, making it important to showcase your qualifications effectively. As a director, you should emphasize your leadership skills, strategic thinking, and ability to drive results within an organization. To help clarify what makes a strong resume summary for this role, we’ll provide examples that illustrate both effective and ineffective approaches:
As a seasoned director, I have extensive experience in various industries. I'm seeking a position where my leadership skills can shine and contribute to the company's success. A supportive environment with career advancement opportunities is what I am looking for. Given the chance, I know I can make a meaningful impact.
- Lacks specific details about past achievements or areas of expertise
- Uses personal preferences instead of focusing on how they can benefit the employer
- Relies on generic statements that do not differentiate from other applicants
Results-driven director with over 10 years of experience in strategic management and operational improvements within healthcare organizations. Spearheaded initiatives that increased patient satisfaction scores by 20% and reduced costs by 15% through effective resource allocation and process optimization. Proficient in budget management, team leadership, and implementing quality assurance measures to improve service delivery.
- Begins with the specific years of experience and role expertise, establishing credibility
- Highlights quantifiable achievements that showcase a direct impact on both patient satisfaction and operational efficiency
- Mentions relevant skills like budget management and team leadership that are critical for a director position
Pro Tip
Showcasing Your Work Experience
The work experience section is important for your resume as a director, where you will find the bulk of your content. Good resume templates always emphasize this key area.
Organized in reverse-chronological order, this section should list your previous roles and responsibilities. Use bullet points to highlight specific achievements and contributions that demonstrate your leadership capabilities.
To illustrate effective entries, we’ve prepared examples that showcase what works well and what can detract from your professional narrative:
Director
Innovative Solutions Inc. – New York, NY
- Managed a team.
- Oversaw projects and tasks.
- Attended meetings regularly.
- Handled budgets and reports.
- Lacks specific accomplishments or metrics to demonstrate impact
- Bullet points are too general and do not highlight unique skills
- Does not mention leadership results or team performance improvements
Director
Tech Innovations Inc. – San Francisco, CA
March 2020 - Present
- Lead a team of 15 in developing cutting-edge software solutions, improving operational efficiency by 30%.
- Implemented strategic initiatives that increased annual revenue by $2 million within the first year.
- Foster collaborative partnerships across departments to drive innovation and ensure project alignment with company goals.
- Uses powerful action verbs to emphasize leadership and impact
- Incorporates specific financial metrics demonstrating significant contributions to the company’s success
- Highlights collaboration skills essential for a director's role, showcasing effective teamwork
While the resume summary and work experience are important components, it's important not to overlook the other sections that contribute to a polished presentation. For further guidance on crafting a standout resume, be sure to explore our comprehensive guide on how to write a resume.
Top Skills to Include on Your Resume
A skills section is important for your resume as it provides a snapshot of your qualifications. It allows you to quickly convey to potential employers that you possess the technical skills and essential competencies needed for the role.
As a director, highlight both leadership and technical skills. Include specific examples such as project management software, budgeting tools, and strategic planning frameworks that showcase your ability to lead effectively.
In addition, soft skills such as leadership, conflict resolution, and communication play an important role in fostering teamwork and ensuring a positive environment for both staff and patients.
Choosing the appropriate resume skills is key to meeting employer expectations and ensuring your application navigates automated screening systems successfully. Companies frequently use specific criteria to weed out job seekers who lack essential skills, so it's important to tailor your skills accordingly.
To effectively highlight your qualifications, carefully examine job postings for insights into which skills are most valued by recruiters. This strategy will help you concentrate on the competencies that attract attention and satisfy ATS requirements.
Pro Tip
10 skills that appear on successful director resumes
Highlighting key skills in your resume can significantly increase your chances of attracting recruiters for director positions. These sought-after skills are evident in our resume examples, allowing you to apply with the assurance that a well-crafted resume provides.
Here are 10 essential skills that should be included in your resume if they align with your expertise and job specifications:
Strategic planning
Staff development
Decision-making
Problem-solving
Operations management
Analytical thinking
Verbal and written communication
Team building
Team collaboration
Creativity and innovation
Based on analysis of 5,000+ film professional resumes from 2023-2024
Resume Format Examples
Selecting the appropriate resume format is important as it showcases your most relevant achievements, skills, and career growth, making a compelling case for your candidacy in a competitive job market.
Functional
Focuses on skills rather than previous jobs
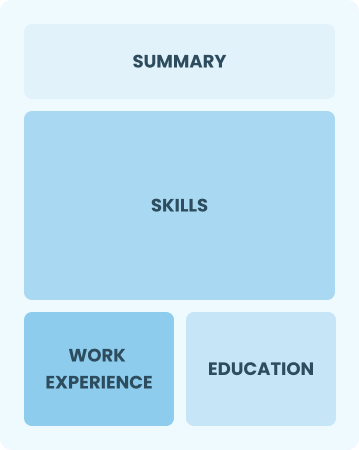
Best for:
Recent graduates or career changers with up to two years of experienc
Combination
Balances skills and work history equally
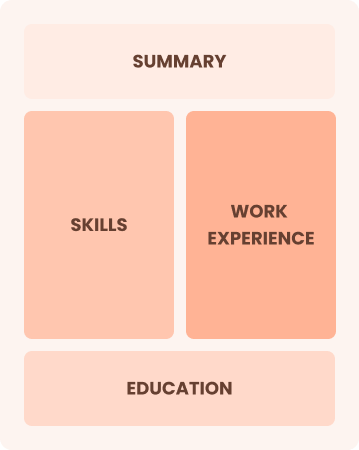
Best for:
Mid-career directors focused on showing their skills and pursuing growth opportunities
Chronological
Emphasizes work history in reverse order

Best for:
Seasoned directors leading innovative techniques and managing film crews
Director Salaries in the Highest-Paid States
Our director salary data is based on figures from the U.S. Bureau of Labor Statistics (BLS), the authoritative source for employment trends and wage information nationwide.
Whether you're entering the workforce or considering a move to a new city or state, this data can help you gauge what fair compensation looks like for directors in your desired area.
Frequently Asked Questions
Should I include a cover letter with my director resume?
Absolutely, including a cover letter can significantly improve your application by showcasing your enthusiasm and providing insight into your qualifications. It allows you to connect your experience directly to the job. If you need assistance, our resources on how to write a cover letter are available to guide you through the process and help create a standout document. You can also use our Cover Letter Generator for crafting an impressive cover letter efficiently.
Can I use a resume if I’m applying internationally, or do I need a CV?
When applying for jobs internationally, a CV is often required instead of a resume. A CV provides a comprehensive overview of your academic and professional history. To assist you, we offer resources on how to write a CV effectively, including formatting tips to create a standout document that aligns with global expectations. You can also explore various CV examples to better understand how to tailor your document for different roles.
What soft skills are important for directors?
Soft skills such as leadership, communication, and conflict resolution are essential for a director. These interpersonal skills foster strong relationships with team members, improve collaboration, and drive organizational success by creating a positive work environment.
I’m transitioning from another field. How should I highlight my experience?
Highlight your transferable skills such as strategic thinking, team collaboration, and effective communication when applying for director roles. These competencies showcase your potential impact even if your experience is in a different sector. Provide concrete examples from past roles to illustrate how your achievements align with the responsibilities of a director, reinforcing your value to prospective employers.
Where can I find inspiration for writing my cover letter as a director?
For aspiring directors, exploring cover letter examples can be invaluable. These samples offer creative content ideas, formatting tips, and effective ways to showcase your qualifications. Use them as a guide to craft an engaging application that stands out in the competitive job market.
Should I include a personal mission statement on my director resume?
Yes, including a personal mission statement on your resume is highly recommended. It effectively communicates your core values and career aspirations, which is especially useful for organizations that prioritize alignment with their mission or have a strong cultural focus.







