Hard skills are technical proficiencies, including threat analysis, network security protocols, and incident response, which are essential for safeguarding information systems.
Popular Information Security Analyst Resume Examples
Check out our top information security analyst resume examples that emphasize key skills such as risk assessment, cybersecurity solutions, and incident response. These examples demonstrate how to effectively showcase your expertise to potential employers.
Ready to create your own impressive resume? Our Resume Builder offers user-friendly templates designed specifically for professionals in the field of information security.
Recommended
Entry-level information security analyst resume
This entry-level resume effectively highlights the job seeker's technical skills and relevant accomplishments in cybersecurity roles, demonstrating a strong foundation in vulnerability assessments and incident response. New professionals must showcase their ability to implement security measures and communicate technical information clearly to appeal to employers despite their limited work experience.
Mid-career information security analyst resume
This resume effectively showcases the job seeker's key qualifications by detailing powerful achievements and technical skills. The structured presentation of their experiences indicates a clear progression, highlighting readiness for advanced roles in information security with a focus on risk management and compliance.
Experienced information security analyst resume
This resume's work history section illustrates the applicant's extensive experience as an information security analyst, emphasizing a 99% security compliance rate and a 40% reduction in incident response time. The clear bullet point format improves readability, making it effective for hiring managers seeking quantifiable achievements.
Resume Template—Easy to Copy & Paste
Sophia Singh
Riverview, FL 33586
(555)555-5555
Sophia.Singh@example.com
Skills
- Network Security
- Vulnerability Assessment
- Risk Management
- Firewall Configuration
- Threat Analysis
- Cybersecurity Protocols
- Incident Response
- Security Audits
Languages
- Spanish - Beginner (A1)
- French - Intermediate (B1)
- German - Beginner (A1)
Professional Summary
Accomplished Information Security Analyst with 7 years' expertise in cybersecurity. Proven track record of reducing incidents using threat analysis and risk management. Skilled in incident response and network security.
Work History
Information Security Analyst
CyberDefend Solutions - Riverview, FL
January 2023 - October 2025
- Reduced security incidents by 30% annually.
- Implemented firewall solutions minimizing threats.
- Trained 50+ staff on cybersecurity protocols.
Cybersecurity Specialist
SecureNet Technologies - Miami, FL
January 2020 - December 2022
- Enhanced security audits by 25% efficiency.
- Detected and resolved 100+ vulnerabilities.
- Managed firewall configurations for networks.
Security Analyst
DataSafe Inc. - Riverview, FL
January 2018 - December 2019
- Conducted risk assessments on 200 systems.
- Developed security policies improving compliance.
- Monitored systems, reducing breaches by 15%.
Certifications
- Certified Information Systems Security Professional (CISSP) - ISC2
- Certified Ethical Hacker (CEH) - EC-Council
Education
Master of Science Information Security
Stanford University Stanford, California
June 2017
Bachelor of Science Computer Science
University of California, Berkeley Berkeley, California
June 2015
How to Write an Information Security Analyst Resume Summary
Your resume summary is the first impression employers will have of you, making it essential to showcase your qualifications effectively. As an information security analyst, you should highlight your technical skills, experience with cybersecurity protocols, and ability to assess risks.
In this field, it's important to convey your expertise in safeguarding data and managing security incidents. Focus on demonstrating your problem-solving abilities and how you've contributed to previous organizations' security measures.
To improve your understanding of effective resume summaries, review the following examples. They will illustrate what resonates well with hiring managers and what pitfalls to avoid:
I am an information security analyst with extensive experience in the field. I want to find a job where I can use my skills and help the company achieve its goals. Ideally, I’m looking for a position that offers good benefits and chances for advancement. I believe I would be a great addition to any team.
- Contains broad statements about experience without detailing specific skills or achievements
- Overuses personal language, making it sound less professional and more self-centered
- Emphasizes what the job seeker seeks from the role rather than highlighting their unique contributions to potential employers
Detail-oriented information security analyst with 6+ years of experience in risk assessment and mitigation, ensuring robust cybersecurity measures for financial institutions. Successfully decreased security incidents by 30% through the implementation of advanced monitoring systems and employee training programs. Proficient in threat analysis, firewalls, and compliance regulations such as GDPR and HIPAA.
- Starts with clear experience duration and area of expertise in cybersecurity
- Highlights quantifiable achievement that showcases effectiveness in reducing security risks
- Mentions specific technical skills relevant to the information security field, improving credibility
Pro Tip
Showcasing Your Work Experience
The work experience section is important on your resume as an information security analyst, where you'll present the bulk of your content. Good resume templates always highlight this important area.
This section should be organized in reverse-chronological order, detailing your prior roles. Use bullet points to succinctly showcase your achievements and responsibilities in each position.
To illustrate what makes a strong work history entry, we’ll provide some examples that demonstrate effective strategies and common pitfalls:
Information Security Analyst
Tech Solutions Inc. – San Francisco, CA
- Monitored security alerts
- Assisted in maintaining systems
- Worked with team on security incidents
- Helped with user training
- Lacks specific employment dates
- Bullet points are vague and do not showcase achievements
- Emphasizes basic tasks instead of measurable impacts or results
Information Security Analyst
TechGuard Solutions – San Francisco, CA
March 2020 - Current
- Conduct regular security audits and risk assessments, identifying vulnerabilities which led to a 40% reduction in security incidents over two years
- Develop and implement comprehensive information security policies that improved compliance with industry regulations and improved data protection measures
- Lead incident response team during cybersecurity breaches, swiftly mitigating threats and restoring services within an average of 3 hours
- Starts each bullet with dynamic action verbs that clearly communicate the applicant's achievements
- Incorporates specific metrics to quantify success, demonstrating the impact of the job seeker's efforts
- Highlights relevant skills such as policy development and incident management that are important for the role
While your resume summary and work experience are important components, don't overlook the importance of other sections. Each part plays a role in presenting your qualifications effectively. For a detailed breakdown, refer to our comprehensive guide on how to write a resume.
Top Skills to Include on Your Resume
A well-structured skills section is important for an information security analyst's resume. It quickly communicates to potential employers that you possess the necessary qualifications and expertise for the role.
Employers are looking for candidates who are well-rounded professionals with key industry expertise and in-demand interpersonal skills. When writing your resume, ensure you showcase your full range of abilities with a mix of hard and soft skills.
Meanwhile, soft skills like critical thinking, attention to detail, and effective communication are important for team collaboration and ensuring comprehensive security measures.
When selecting skills for your resume, it’s important to align them with what employers expect from an ideal applicant. Many organizations use automated screening systems that filter out applicants lacking essential resume skills, making this alignment important.
To improve your chances of success, review job postings closely for insights into desired skills. This approach will help you prioritize the most relevant abilities and ensure your resume stands out to both recruiters and ATS systems alike.
Pro Tip
10 skills that appear on successful information security analyst resumes
Make your resume stand out to recruiters by highlighting the essential skills that information security analysts need. You’ll find examples of these skills showcased in our resume examples, helping you present yourself with confidence to potential employers.
Here are 10 vital skills you should consider adding to your resume if they match your qualifications and job requirements:
Risk assessment
Incident response
Network security protocols
Firewall management
Malware analysis
Data encryption techniques
Security audits
Vulnerability assessment tools
User training and awareness
Regulatory compliance knowledge
Based on analysis of 5,000+ information technology professional resumes from 2023-2024
Resume Format Examples
Selecting the appropriate resume format is important for an information security analyst as it effectively showcases your technical skills, relevant experience, and career advancements in cybersecurity.
Functional
Focuses on skills rather than previous jobs
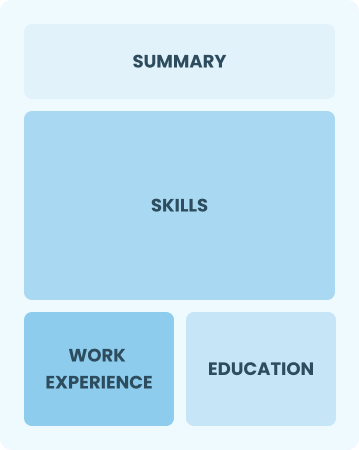
Best for:
Recent graduates and career changers with up to two years of experience
Combination
Balances skills and work history equally
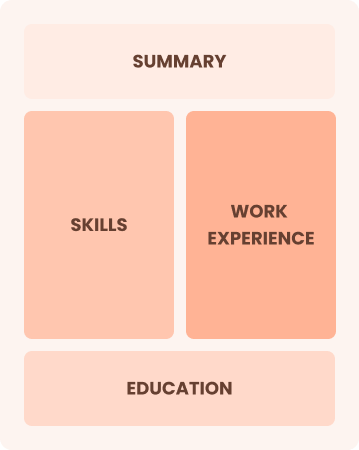
Best for:
Mid-career professionals focused on demonstrating their skill set and growth potential
Chronological
Emphasizes work history in reverse order

Best for:
Seasoned experts leading cybersecurity initiatives and risk management strategies
Information Security Analyst Salaries in the Highest-Paid States
Our information security analyst salary data is based on figures from the U.S. Bureau of Labor Statistics (BLS), the authoritative source for employment trends and wage information nationwide.
Whether you're entering the workforce or considering a move to a new city or state, this data can help you gauge what fair compensation looks like for information security analysts in your desired area.
Frequently Asked Questions
Should I include a cover letter with my information security analyst resume?
Absolutely! Including a cover letter with your application can significantly improve your chances of making a strong impression on recruiters. It allows you to highlight your relevant skills and convey your enthusiasm for the position. If you need assistance, our guide on how to write a cover letter is a great starting point. You can also use our Cover Letter Generator for quick help in creating one that stands out.
Can I use a resume if I’m applying internationally, or do I need a CV?
For international job applications, use a CV instead of a resume when applying in regions like Europe or Asia where detailed career histories and qualifications are valued. Explore our CV examples and guides to ensure your document aligns with global expectations. You can learn more about how to write a CV to make sure it meets the standards required in these regions.
What soft skills are important for information security analysts?
Soft skills such as interpersonal skills, problem-solving, communication, and teamwork are essential for information security analysts. These abilities facilitate collaboration with colleagues and assist in effectively conveying security strategies to non-technical stakeholders, ultimately fostering a safer organizational environment.
I’m transitioning from another field. How should I highlight my experience?
Highlight your transferable skills, such as analytical thinking, teamwork, and attention to detail, from your previous roles. These qualities showcase your ability to adapt and add value in the information security field. Use specific instances where you've solved problems or improved processes to illustrate how your background aligns with key responsibilities in this role.
How should I format a cover letter for a information security analyst job?
To format a cover letter, begin with your name and contact details. Follow this with a professional salutation. Capture attention in the opening paragraph by highlighting relevant skills or experiences. Include a summary of your qualifications that aligns with the job description. Tailoring your content to specific requirements demonstrates genuine interest and improves your chances of standing out.
How do I add my resume to LinkedIn?
To improve your resume’s visibility on LinkedIn, you should add your resume to LinkedIn directly to your profile or highlight relevant skills and achievements in the "About" and "Experience" sections. This approach helps recruiters and hiring managers easily identify qualified information security analysts like you.







