When working as a security control assessor, it's important to emphasize hard skills like risk assessment, security testing, and compliance evaluation.
Popular Security Control Assessor Resume Examples
Check out our top security control assessor resume examples that demonstrate critical skills like risk management, compliance analysis, and security assessments. These resumes highlight how to effectively communicate your accomplishments in the field.
Ready to build your own impressive resume? Our Resume Builder offers user-friendly templates specifically designed for security professionals, helping you make a strong impression in your job search.
Recommended
Entry-level security control assessor resume
This entry-level resume for a security control assessor effectively highlights the job seeker's hands-on experience in security policy evaluation and penetration testing, showcasing a solid foundation in cybersecurity practices. New professionals in this field must demonstrate their technical skills and relevant certifications, illustrating their ability to contribute to organizational security despite limited professional experience.
Mid-career security control assessor resume
This resume effectively showcases the job seeker's qualifications, demonstrating significant achievements in security assessments and compliance. The structured presentation of experiences highlights their readiness for leadership roles and complex challenges in cybersecurity, underscoring a strong career trajectory.
Experienced security control assessor resume
This resume illustrates the applicant's strong background in cybersecurity, demonstrating their expertise as a security control assessor. Key achievements include achieving a 98% success rate in compliance programs and improving incident response time by 30%, with the clear formatting improving readability for hiring managers.
Resume Template—Easy to Copy & Paste
Li Rodriguez
Eastside, WA 98010
(555)555-5555
Li.Rodriguez@example.com
Professional Summary
Seasoned Security Control Assessor with 9 years of experience in enhancing security protocols and compliance. Proven expert in conducting audits, reducing risks, and managing incident responses to safeguard data integrity. Exceptional skills in assessments and vulnerability management.
Work History
Security Control Assessor
SecureTech Solutions - Eastside, WA
January 2023 - November 2025
- Assessed 50+ security controls monthly
- Improved compliance by 30% in Q1
- Conducted 15 security audits quarterly
Information Security Analyst
CyberSafe Inc. - Eastside, WA
January 2018 - December 2022
- Reduced vulnerabilities by 25% over two years
- Managed incident response for 20+ cases
- Reviewed 100+ security log entries daily
Risk Management Specialist
DataGuard Partners - Silverlake, WA
January 2016 - December 2017
- Identified risks, reducing events by 40%
- Developed 10 risk assessment guides
- Implemented a risk matrix for projects
Skills
- Risk Assessment
- Security Audits
- Incident Response
- Vulnerability Management
- Control Testing
- Compliance Improvement
- Security Policies
- Data Protection
Certifications
- Certified Information Systems Security Professional - ISC2
- Certified Ethical Hacker - EC-Council
Education
Master of Science Cybersecurity
George Mason University Fairfax, Virginia
June 2015
Bachelor of Science Information Systems
James Madison University Harrisonburg, Virginia
June 2013
Languages
- Spanish - Beginner (A1)
- French - Beginner (A1)
- Mandarin - Beginner (A1)
How to Write a Security Control Assessor Resume Summary
Your resume summary is the first impression potential employers have of you, so it’s important to make it count by showcasing your fit for the security control assessor role. This section should highlight your analytical skills and understanding of compliance regulations, emphasizing your capability in risk management.
As a security control assessor, you will want to underline your experience with security assessments and ability to communicate findings effectively. Highlighting relevant certifications and technical expertise can set you apart from other job seekers.
To help clarify what makes an effective summary, we’ve provided examples that illustrate both strong and weak approaches:
I am a dedicated security control assessor with several years in the field. I want to find a job where I can use my skills and help companies stay secure. A position that allows for teamwork and personal development is what I’m looking for. I believe I would be a great asset if given the chance.
- Lacks specific examples of skills or experiences relevant to security control assessment, making it too vague
- Focuses on what the job seeker desires from the job rather than highlighting their unique contributions
- Uses generic phrases like "great asset" without demonstrating any concrete value or achievements
Detail-oriented Security Control Assessor with over 6 years of experience in risk management and compliance evaluation within federal and private sectors. Successfully implemented security frameworks that improved audit readiness by 30% and reduced vulnerabilities by 20% through rigorous assessments and remediation strategies. Proficient in NIST SP 800-53, Risk Management Framework (RMF), and continuous monitoring practices.
- Begins with a clear statement of experience level and area of expertise
- Incorporates quantifiable achievements that showcase measurable improvements in compliance and security posture
- Highlights relevant technical skills that are critical for the role of a Security Control Assessor
Pro Tip
Showcasing Your Work Experience
The work experience section is the cornerstone of your resume as a security control assessor. This is where you’ll convey the bulk of your professional journey, and good resume templates always prioritize this important area.
Organize this section in reverse-chronological order, detailing your previous roles. Use bullet points to highlight key achievements and responsibilities for each position you’ve held.
To help clarify what makes an effective work history section, we will present a couple of examples that demonstrate best practices and common pitfalls:
Security Control Assessor
TechSecure Solutions – Atlanta, GA
- Reviewed security policies.
- Conducted assessments.
- Collaborated with teams.
- Documented findings.
- Lacks specific details about assessment methods used
- Bullet points are vague and do not highlight unique skills or achievements
- Does not mention any measurable outcomes or improvements resulting from the role
Security Control Assessor
TechSecure Solutions – Austin, TX
March 2020 - Current
- Conduct comprehensive security assessments for client systems, identifying vulnerabilities and recommending corrective actions that improved security posture by 40%.
- Develop and implement risk management frameworks, leading to a 30% reduction in compliance violations over one year.
- Train staff on security protocols and best practices, increasing awareness and adherence to security guidelines among employees.
- Starts each bullet with strong action verbs to clearly convey the applicant’s contributions
- Incorporates specific metrics that quantify the impact of the applicant’s efforts
- Highlights relevant skills like risk management and training, essential for a Security Control Assessor's role
While your resume summary and work experience are important components, don't overlook the importance of other sections that improve your qualifications. For detailed guidance on crafting a well-rounded resume, explore our comprehensive guide on how to write a resume.
Top Skills to Include on Your Resume
A well-defined skills section is important for a strong resume, as it allows you to showcase your technical skills at a glance. This section helps employers quickly assess whether you possess the essential abilities needed for the role.
As a security control assessor, highlight both interpersonal and technical skills in your resume. Include specific examples such as risk assessment tools, compliance frameworks, and familiarity with security software like Nessus or Splunk to demonstrate your expertise.
Additionally, soft skills such as critical thinking, attention to detail, and effective communication are essential for collaborating with teams and ensuring robust security measures are implemented successfully.
Selecting the right resume skills is important for aligning with what employers expect from applicants. Many organizations employ automated screening systems to filter out applicants lacking essential skills, making it necessary to tailor your resume accordingly.
To effectively highlight your qualifications, examine job postings closely. They often reveal the specific resume skills that recruiters and ATS systems prioritize, helping you emphasize the most relevant abilities on your resume.
Pro Tip
10 skills that appear on successful security control assessor resumes
Improve your resume to attract recruiters by highlighting essential skills that are in high demand for security control assessors. You can see these skills effectively showcased in our resume examples, which help you apply with the confidence a tailored resume provides.
Here are 10 skills you should consider incorporating into your resume if they align with your experience and job expectations:
Risk assessment
Attention to detail
Analytical thinking
Report writing
Knowledge of regulatory standards
Incident response planning
Vulnerability assessment
Project management
Communication skills
Team collaboration
Based on analysis of 5,000+ safety security professional resumes from 2023-2024
Resume Format Examples
Selecting the appropriate resume format is important for security control assessors, as it effectively showcases critical skills, relevant experience, and career advancement in a clear and engaging manner.
Functional
Focuses on skills rather than previous jobs
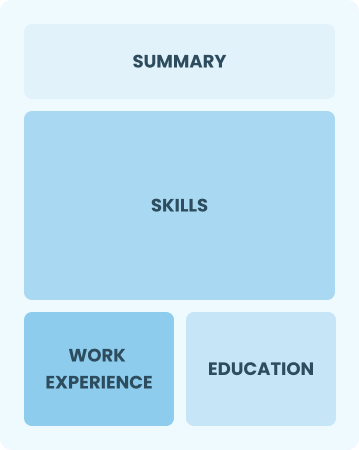
Best for:
Recent graduates and career changers with up to two years of experience
Combination
Balances skills and work history equally
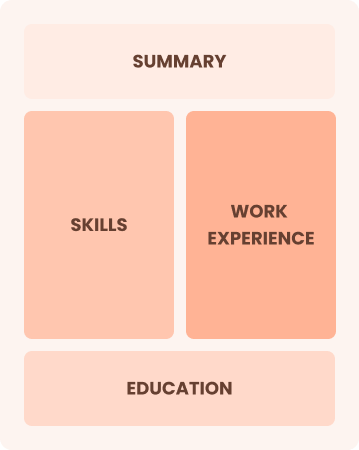
Best for:
Mid-career professionals focused on demonstrating their skills and seeking growth opportunities
Chronological
Emphasizes work history in reverse order

Best for:
Experts in risk management and compliance leadership
Frequently Asked Questions
Should I include a cover letter with my security control assessor resume?
Absolutely, including a cover letter is essential for making a strong impression on hiring managers. It allows you to highlight your unique qualifications and demonstrate your enthusiasm for the position. If you're looking for tips on crafting the perfect cover letter, check out our comprehensive guide on how to write a cover letter. Alternatively, you can use our easy-to-navigate Cover Letter Generator to get started quickly.
Can I use a resume if I’m applying internationally, or do I need a CV?
When applying for jobs outside the U.S., it's important to use a CV instead of a resume. A CV provides a comprehensive overview of your academic background and work history, which many employers prefer internationally. Explore how to write a CV to ensure your document meets global expectations, and take advantage of our CV examples for additional guidance.
What soft skills are important for security control assessors?
Soft skills like critical thinking, collaboration, and communication are essential for security control assessors. These interpersonal skills enable effective teamwork and clear reporting, fostering a culture of security awareness and ensuring comprehensive risk assessments within organizations.
I’m transitioning from another field. How should I highlight my experience?
Highlight your transferable skills such as analytical thinking, communication, and attention to detail from previous roles. These abilities showcase your potential to excel as a security control assessor, even if you lack direct experience. Use concrete examples to illustrate how your past successes align with key responsibilities in this field.
Where can I find inspiration for writing my cover letter as a security control assessor?
For those applying for security control assessor positions, exploring professionally crafted cover letter examples can provide valuable inspiration. These samples offer insights into effective content ideas, formatting techniques, and ways to highlight your qualifications compellingly. Use them to improve your application materials and stand out in the job market.
How do I add my resume to LinkedIn?
To boost your resume's visibility on LinkedIn, you should add your resume to LinkedIn by uploading it to your profile or by highlighting key skills and experiences in the "About" and "Experience" sections. This strategy helps security recruiters easily locate qualified job seekers, increasing your discoverability for relevant job opportunities.







