Hard skills such as data analysis, risk modeling, and expertise in statistical software help risk analysts evaluate and mitigate potential risks effectively.
Popular Risk Analyst Resume Examples
Check out our top risk analyst resume examples that emphasize critical skills such as data analysis, risk assessment, and financial modeling. These resumes are designed to help you effectively showcase your qualifications in a competitive job market.
Looking to build your own impressive resume? The Resume Builder offers user-friendly templates tailored for finance professionals, making it simple to highlight your strengths.
Recommended
Entry-level risk analyst resume
This entry-level resume for a risk analyst effectively highlights the applicant's analytical skills and achievements from previous roles, including measurable improvements in risk assessment accuracy and operational efficiency. New professionals in this field must demonstrate a strong understanding of risk management principles and relevant technical competencies through their resume, even if their work history is limited.
Mid-career risk analyst resume
This resume effectively showcases the applicant's analytical expertise and achievement-driven mindset, indicating readiness for advanced risk management roles. The progression through increasingly responsible positions highlights their capability to tackle complex financial challenges while leading powerful initiatives.
Experienced risk analyst resume
This work history section highlights the applicant's extensive experience as a Risk Analyst, showcasing achievements like reducing portfolio risk by 15% and saving $200k annually through effective model implementation. The clear bullet-point format improves readability, making it ideal for hiring managers looking for quick insights into accomplishments.
Resume Template—Easy to Copy & Paste
Daniel Zhang
Tacoma, WA 98408
(555)555-5555
Daniel.Zhang@example.com
Skills
- Risk Analysis
- Financial Modeling
- Data Interpretation
- Risk Management
- Quantitative Analysis
- Compliance Management
- Strategic Planning
- Risk Mitigation
Languages
- Spanish - Beginner (A1)
- French - Beginner (A1)
- German - Intermediate (B1)
Professional Summary
Dynamic risk analyst with 9 years of experience in optimizing risk management protocols, forecasting financial trends, and achieving significant cost reductions. Proficient in quantitative analysis and compliance management, with proven results in enhancing organizational safety and financial stability.
Work History
Risk Analyst
Innovative Risk Solutions - Tacoma, WA
May 2023 - January 2026
- Developed risk models increasing prediction by 33%
- Implemented a risk assessment protocol saving 1.2M
- Analyzed portfolios and reduced risks by 25%
Safety and Risk Consultant
Pioneer Risk Management - Eastside, WA
May 2019 - April 2023
- Designed safety audits lowering incidents by 20%
- Enhanced compliance training cutting violations by 15%
- Led team to achieve ISO certification in 6 months
Financial Risk Officer
Fidelity Secure Finance - Seattle, WA
May 2014 - May 2019
- Streamlined risk reporting reducing errors by 40%
- Forecasted financial trends boosting investments by 30%
- Collaborated with teams cutting response times by 50%
Certifications
- Certified Risk Manager - Global Risk Management Institute
- Financial Risk Certification - International Finance Institute
Education
Master of Science Finance
University of California, Berkeley Berkeley, California
June 2014
Bachelor of Science Economics
University of Washington Seattle, Washington
June 2012
How to Write a Risk Analyst Resume Summary
Your resume summary is the first section hiring managers will see, making it essential to craft a compelling introduction that highlights your qualifications. As a risk analyst, you should emphasize your analytical skills, attention to detail, and ability to assess potential risks effectively. The following examples will illustrate effective strategies for creating a strong resume summary:
I am a dedicated risk analyst with years of experience in financial services. I want to find a position where I can use my analytical skills and contribute to team goals. A company that values employee development and offers great benefits would be perfect for me. I believe I can help improve the team's performance if given the chance.
- Lacks specific examples of skills or experiences, making it unclear what the job seeker truly brings to the table
- Overuses personal pronouns, which detracts from professionalism and makes it feel less effective
- Emphasizes what the applicant seeks instead of articulating how they can add value to potential employers
Analytical risk analyst with over 6 years of experience in financial services, focusing on market risk assessment and compliance analysis. Successfully reduced potential losses by 20% through advanced quantitative modeling and risk mitigation strategies. Proficient in using statistical software, conducting stress testing, and interpreting complex data to inform strategic decision-making.
- Begins with clear indication of experience level and area of expertise
- Highlights quantifiable achievement that showcases significant impact on financial performance
- Mentions relevant technical skills and tools that align with industry requirements
Pro Tip
Showcasing Your Work Experience
The work experience section is important for your resume as a risk analyst, containing the bulk of your content. Good resume templates always feature this important section prominently.
This part should be organized in reverse-chronological order, highlighting your previous roles and responsibilities. Use bullet points to succinctly describe your key achievements and contributions in each position.
To guide you further, we’ll present a couple of examples that effectively illustrate what works and what to avoid in a risk analyst's work history section:
Risk Analyst
XYZ Financial Services – New York, NY
- Analyzed financial data.
- Prepared reports for management.
- Collaborated with team members.
- Assisted in risk assessments.
- Lacks specific achievements or metrics to demonstrate impact
- Bullet points are overly simplistic and do not showcase unique skills
- Does not clarify the context of roles or responsibilities within the company
Risk Analyst
Global Financial Services – New York, NY
March 2020 - Current
- Conduct comprehensive risk assessments for investment portfolios, identifying potential threats and opportunities that improved decision-making efficiency by 30%.
- Develop quantitative models to predict market fluctuations, improving predictive accuracy by 25% over two years.
- Collaborate with the compliance team to ensure regulatory adherence, resulting in zero compliance issues during audits.
- Starts each bullet with strong action verbs that highlight the applicant's contributions
- Incorporates specific metrics to quantify achievements and showcase effectiveness
- Demonstrates relevant skills such as analytical thinking and collaboration within a professional context
While your resume summary and work experience are important, don't overlook the significance of other sections. Each part contributes to a well-rounded presentation of your skills and qualifications. For more detailed guidance, be sure to explore our comprehensive guide on how to write a resume.
Top Skills to Include on Your Resume
A well-crafted skills section is a vital component of any effective resume. It provides job seekers with the opportunity to showcase their qualifications and demonstrates to employers that they possess the necessary competencies for the role.
This section allows hiring managers to quickly evaluate whether job seekers align with job requirements, streamlining the selection process. Risk analyst professionals should highlight both technical and interpersonal skills, which will be discussed in detail below.
Soft skills play a important role for risk analysts, as they foster clear communication, critical thinking, and teamwork. These abilities improve decision-making and improve risk management outcomes.
Selecting the right resume skills is important to align with what employers expect from applicants. Many companies use automated systems that screen for these essential abilities, so your resume must reflect them to pass initial evaluations.
To effectively choose which resume skills to highlight, review job postings closely. These listings often provide specific guidance on the skills recruiters prioritize, helping ensure your application meets both their preferences and ATS requirements.
Pro Tip
10 skills that appear on successful risk analyst resumes
Improving your resume with sought-after skills can significantly attract the attention of recruiters in the risk analyst field. You’ll discover these essential qualifications highlighted in our resume examples, empowering you to pursue opportunities confidently.
By the way, here are 10 skills you should consider incorporating into your resume if they align with your experience and job requirements:
Risk assessment
Analytical thinking
Attention to detail
Problem-solving
Data analysis
Communication skills
Regulatory knowledge
Financial modeling
Project management
Team collaboration
Based on analysis of 5,000+ finance professional resumes from 2023-2024
Resume Format Examples
Choosing the right resume format is important for a risk analyst because it clearly highlights key analytical skills, relevant experience, and career growth effectively.
Functional
Focuses on skills rather than previous jobs
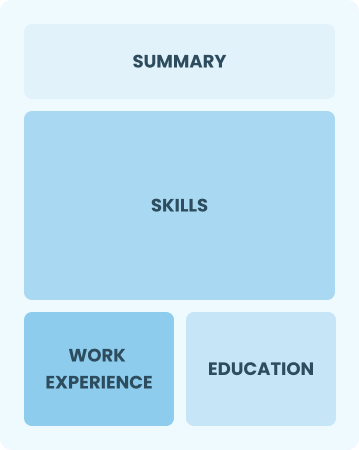
Best for:
Recent graduates and career changers with limited experience in risk analysis
Combination
Balances skills and work history equally
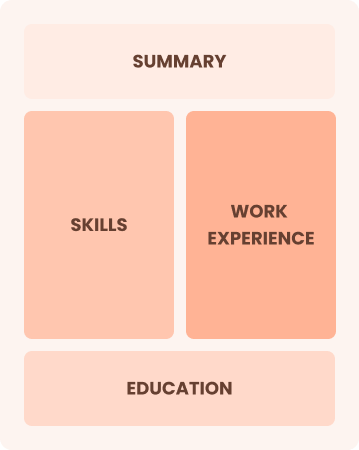
Best for:
Mid-career analysts eager to demonstrate their skills and pursue new opportunities
Chronological
Emphasizes work history in reverse order

Best for:
Seasoned experts leading risk management initiatives and strategy development
Frequently Asked Questions
Should I include a cover letter with my risk analyst resume?
Absolutely, including a cover letter is important to improve your application. It allows you to showcase your personality and clarify how your skills align with the company's needs. If you're looking for assistance, check out our comprehensive guide on how to write a cover letter or use our Cover Letter Generator to craft a professional one effortlessly.
Can I use a resume if I’m applying internationally, or do I need a CV?
When applying for jobs outside the U.S., use a CV instead of a resume. A CV provides a comprehensive overview of your academic and professional history. To assist with formatting and crafting an effective CV, explore our resources on how to write a CV that offer examples and tips tailored for international applications. Additionally, reviewing CV examples can provide further guidance.
What soft skills are important for risk analysts?
Soft skills, including analytical thinking and attention to detail like effective communication, are essential for risk analysts. These interpersonal skills help you interpret data accurately, collaborate with teams, and convey complex findings clearly, fostering strong connections with stakeholders and improving decision-making processes.
I’m transitioning from another field. How should I highlight my experience?
When transitioning to a risk analyst role, emphasize transferable skills such as analytical thinking, attention to detail, and effective communication from your previous jobs. These abilities illustrate how you can assess risks and develop strategies in this field. Use concrete examples to connect your past successes with the key responsibilities of risk analysis, demonstrating your readiness for the new challenges ahead.
How should I format a cover letter for a risk analyst job?
To format a cover letter for a risk analyst position, start with your contact information at the top. Follow this by adding a professional salutation and an engaging opening that highlights your interest in the role. Clearly outline your relevant skills and experiences, ensuring they align with the job description. Finish with a strong closing statement that encourages the employer to reach out.
Should I use a cover letter template?
Yes, using a cover letter template tailored for risk analysts improves your ability to present complex data analysis skills and relevant certifications clearly, ensuring hiring managers quickly recognize your expertise in risk assessment and mitigation strategies.







